The Laws That Took Down Mobsters Are Being Turned Against Big Oil

This story was originally published by Grist. Sign up for Grist’s weekly newsletter here.

This story was originally published by Grist. Sign up for Grist’s weekly newsletter here.
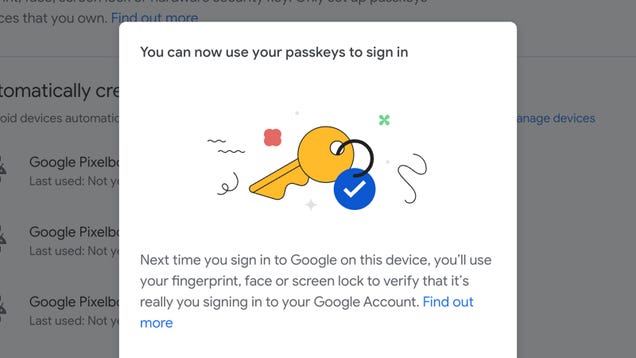
The future is passkeys, not passwords: Google accounts are the latest to make the switch, following similar moves by Apple and Microsoft over the last couple of years (with other smaller names also making the switch). It means more convenience and more security for your account, and no need to have to remember dozens…

TikTokers in Montana are going to war against a new law banning the app across the state. They’re banding together and joining lawsuits against the state, accusing their elected officials of suppressing their speech and upending their livelihoods.
In 2022, Twitter co-founder Jack Dorsey left the company. One of his new projects, Bluesky, is a social media app that looks exactly like Twitter. The difference? Bluesky promises an unprecedented level of control over your scrolling experience. The goal, essentially, is to undo all of Dorsey’s self-described…

Twitter CEO Elon Musk slammed people who work from home in an interview this week and declared the practice was “morally wrong,” despite the fact that, as head of three companies, it is virtually impossible for him to be in three offices at once. He’s the quintessential remote CEO. Although Musk’s comments dominated…
By Danijela Obradovic, Lawyer at Roberts & Obradovic “Privacy by Design,” a concept first introduced by former Ontario Information and Privacy Commissioner Ann Cavoukian, is a comprehensive approach to privacy […]
The post Understanding The Concept of Privacy By Design appeared first on Cyber Defense Magazine.
The individual in question, who lives in Bucharest, Romania, has been given the codename Jack. He is one of the two criminals operating an account on the Russian-language Exploit.in forum under the name “badbullzvenom,”
By Dotan Nahum, Head of Developer-First Security at Check Point Software Technologies Here’s a quick-fire question: do you know where all your sensitive data is? As businesses of all sizes […]
The post The Data Challenge: How to Map Data in A Distributed World appeared first on Cyber Defense Magazine.
US CISA added the vulnerability CVE-2023-21492 flaw affecting Samsung devices to its Known Exploited Vulnerabilities Catalog. US CISA added the vulnerability CVE-2023-21492 vulnerability (CVSS score: 4.4) affecting Samsung devices to its Known Exploited Vulnerabilities Catalog. The issue affects Samsung mobile devices running Android 11, 12, and 13, it is described as an insertion of sensitive […]
The post US CISA warns of a Samsung vulnerability under active exploitation appeared first on Security Affairs.