Ditch the Worry – Switch to Secure WhatsApp Alternative
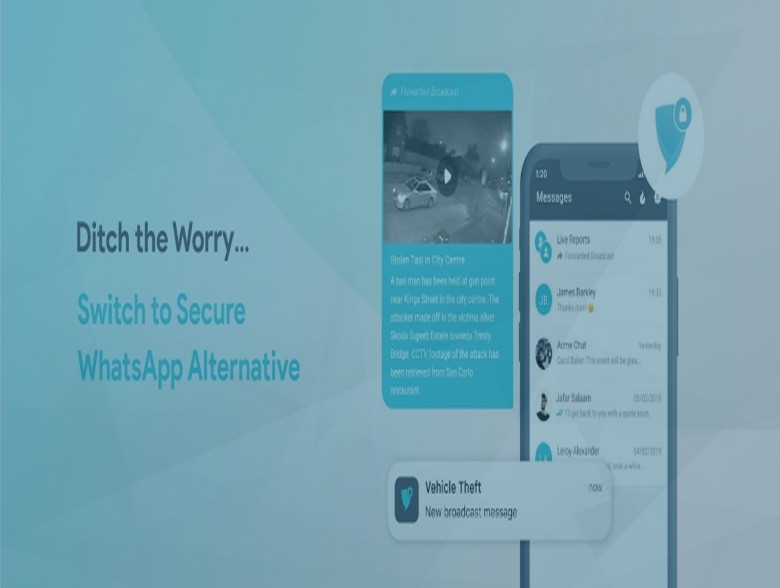
The post Ditch the Worry – Switch to Secure WhatsApp Alternative appeared first on Cyber Defense Magazine.

The post Ditch the Worry – Switch to Secure WhatsApp Alternative appeared first on Cyber Defense Magazine.
The post Protecting Critical Infrastructure from Cyber Attack appeared first on Cyber Defense Magazine.
The post Ruthless Prioritization Is a Myth: Aim For Risk-Less Prioritization Instead appeared first on Cyber Defense Magazine.
The Importance of Choosing the Right Privilege Identity Management Solution The essence of effective Privileged Identity Management (PIM) lies not in identity or management but in privilege. A robust PIM system focuses on identifying those who should, and equally importantly, those who should not, have administrative access to important accounts and systems. This access empowers […]
The post 10 Best Privileged Identity Management Tools (2024) appeared first on Heimdal Security Blog.
In the fast-paced world of IoT4, smart manufacturing is emerging as a game-changer in the manufacturing process. The combination of cutting-edge technology and cutting-edge processes is ushering in a new age of industrialization. Discover the building blocks of Smart Manufacturing, and how they all work together to redefine manufacturing efficiency, productivity, and agility. 1. Digital […]
The post Unlocking The Power Of Smart Manufacturing: 10 Essential Elements appeared first on SecureBlitz Cybersecurity.
Here is the Surfshark Alternative ID review based on first-hand experience. Protecting your online identity is more crucial than ever in today’s digital world. Surfshark, a leading name in the VPN industry, recognizes this need and offers a unique solution known as Alternative ID. Instead of just shielding your online activities, Surfshark takes a step […]
The post Surfshark Alternative ID Review 2024 appeared first on SecureBlitz Cybersecurity.
EXECUTIVE SUMMARY: Cyber criminals are weaponizing advanced tactics, including intricate social engineering campaigns, to carry out malicious activities. Last year, social engineering attempts rose by 464%. Often a result of social engineering attempts, ransomware attacks have reportedly increased by 90%. Amidst this unsettling attack landscape, it can be difficult and stressful to secure data and […]
The post The all-star AI-powered, cloud-delivered security platform you need appeared first on CyberTalk.
Keenan data breach exposes sensitive data belonging to 1,509,616 individuals. The insurance broker company notified the impacted customers and employees on January 26th, 2024. According to the data breach notification, the hackers gained access to Keenan’s network on August 21st, 2023. The company discovered the intrusion a few days later, on August 27th. They opened […]
The post Keenan Data Breach Puts Personal Data Of 1.5 Million People at Risk appeared first on Heimdal Security Blog.
Threat and Vulnerability Management plays a crucial role in safeguarding information systems. It involves identifying, assessing, and mitigating vulnerabilities in software, hardware, and organizational processes. Effective TVM not only anticipates and counters potential cyber threats but also ensures compliance with various security standards, thereby maintaining the integrity, confidentiality, and availability of data. This article serves […]
The post Free and Downloadable Threat & Vulnerability Management Templates appeared first on Heimdal Security Blog.
Cactus Ransomware claims responsibility for the January 17th Schneider Electric data breach. Schneider Electric confirms hackers got access to their Resource Advisor cloud platform. The French-based energy giant says the attack only hit their Sustainability Business division. The platform holds data belonging to more than 2000 companies worldwide. For the moment, there`s no impact on […]
The post Cactus Ransomware behind Schneider Electrics Data Breach appeared first on Heimdal Security Blog.