Fight AI With AI
Seized Genesis malware market’s infostealers infected 1.5 million computers
Infamous hacker marketplace Genesis, which was taken down this week by an international law enforcement operation involving 17 countries, was selling access to millions of victim computers gained via the DanaBot infostealer and likely other malware.
Trellix, the cybersecurity firm that assisted in the takedown of the Genesis site, said that malware used by Genesis provided access to browser fingerprints, cookies, autofill form data, and other credentials.
“The disruption of Genesis Market is yet another successful takedown that proves that public-private partnerships are vital in fighting cybercrime,” said John Fokker, head of threat intelligence at the Trellix Advanced Research Center in Amsterdam. “We had been monitoring the marketplace for many years now and are proud to have been able to play a part in the takedown of this notorious market.”
Let’s Recap Baby Yoda’s Day Out With Dutchess Lizzo on The Mandalorian

The warmest and most welcome addition to the Star Wars universe made her debut on The Mandalorian’s “Guns for Hire” episode.
Google is Finally Bringing Live Translate Captions to Chrome
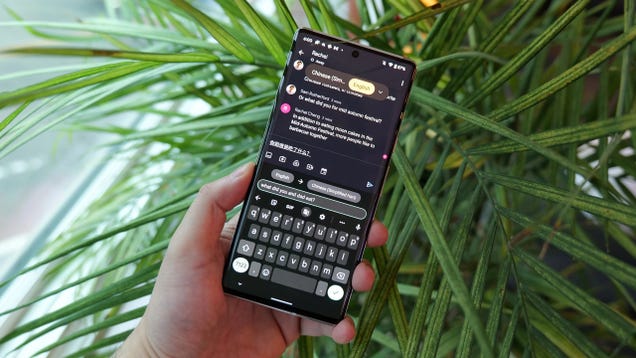
After nearly two years, Chrome browsers may soon finally get a feature that has thus far been restricted to Google Pixel phones. On Thursday, Reddit user and Chrome Canary beta tester Leopeva64 posted several screenshots and GIFs on the r/chrome subreddit showing off an upcoming Live Translate caption feature coming…
This WB100 Merch Is Full of Movie Magic

It’s a big year for Warner Bros. with all its centennial celebrations. Merch marking the WB100 features mash-ups with the Looney Tunes, DC characters, and cinematic classics like Casablanca. The collection also includes special edition items inspired by WB’s 100 years of storytelling—think replicas of iconic props like…
U.S. Chemical Plants Would Have to Make Big Changes Under New EPA Rule

The U.S. Environmental Protection Agency on Thursday proposed new regulation that would make chemical plant owners and operators responsible for their toxic emissions. Facilities would have to measure and reduce hazardous compounds beyond just the property that a chemical plant sits on, a change that could…
Tesla Employees Have Been Sharing and Meme-ing Your Private Car Videos

Former Tesla employees are confessing to sharing, laughing at, playing in slow motion, and generally having a great time watching the videos that were taken with customers’ in-vehicle cameras. Reuters reports that close to a dozen former employees have revealed that sharing drivers’ personal videos was one of their…
JILA’s Frequency Comb Breathalyzer Detects COVID-19 with Excellent Accuracy
Default static key in ThingsBoard IoT platform can give attackers admin access
Developers of ThingsBoard, an open-source platform for managing IoT devices that’s used in various industry sectors, have fixed a vulnerability that could allow attackers to escalate their privileges on a server and send requests with administrative privileges. The vulnerability, tracked as CVE-2023-26462, was discovered and privately reported by researchers from IBM Security X-Force. It stems from the platform using a static key to sign JSON Web Tokens (JWTs) issued to clients. With knowledge of that key, which can be easily obtained, attackers could forge valid requests that would allow them to identify to the system as higher privileged users.
“Because ThingsBoard allowed the default key to be used without requiring administrators to change it, and because that default key was also exposed publicly in the configuration files, the door was opened for attackers to gain unauthorized access in excess of what is intended,” the X-Force researchers said in their report.





