React is a popular JavaScript library used to build modern, interactive web interfaces. It helps developers create UI components that update efficiently when data changes. React runs mostly in the browser, handling:
- UI rendering
- State updates
- User interactions
Next.js is a full-stack framework built on React. It adds server-side capabilities. This allows developers to build faster, more scalable applications where:
- Part of the logic runs in the browser
- Part runs on the server
Next.js manages this hybrid environment automatically, making it easy to deliver high-performance, SEO-friendly websites and complex full-stack applications.
React Server Components (RSC) is a system used by frameworks like Next.js to render parts of a webpage on the server and stream the results to the client. It uses the Flight protocol to exchange serialized component data. This improves performance but also exposes a structured input surface that must be validated, which became the root of CVE-2025-55182.
CVE-2025-55182
CVE-2025-55182 is a deserialization and object traversal vulnerability inside the React Server Component (RSC) protocol, also known as the flight protocol.
RSC allows clients to request server-rendered data using a structured protocol. The server receives multipart form-data describing:
- component state
- functions to invoke
- internal object references
However, the RSC parser did not validate traversal paths, allowing attackers to craft custom paths that intentionally walk through JavaScript’s prototype chain.
This mistake turns a seemingly harmless metadata protocol into a pathway for full server compromise.
Root Cause Analysis
1. The Flight Protocol Accepts Path Markers
React internally uses markers, which are meant to help reconstruct server-side objects.
$1:<object>:<property>
2. Missing Validation
The parser failed to confirm whether paths referenced allowed objects. Attackers discovered they could supply values like:
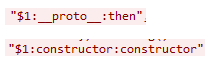
This allows access to JavaScript internals such as:
- object prototypes
- constructors
- built-in function constructors
3. Escalation to Code Execution
Following this path chain leads to the JavaScript Function constructor, effectively allowing execution of arbitrary code:
Function(“payload”)()
Frameworks built on RSC, such as Next.js, were especially at risk because they expose RSC endpoints by default.
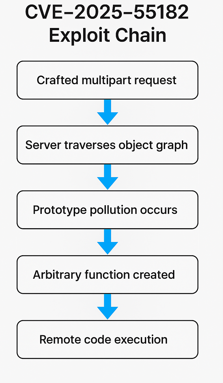
How the Exploit Works (Step-by-Step)
1. The attacker submits a crafted multipart/form-data request
This request includes headers like:
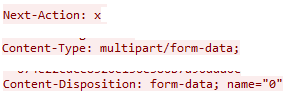
2. Malicious path markers
Inside one of the parts, the attacker includes:
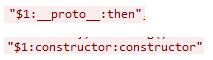
These tell the server to traverse the object graph in dangerous ways.
3. Prototype pollution occurs
The server tries to reconstruct objects, inadvertently applying attacker-controlled paths to server objects.
4. Arbitrary function creation
By navigating through the constructor chain, the attacker reaches:
Function(“payload”)()
5. Full Remote Code Execution
One observed payload (from real-world PoCs) was:
![]()
This directly invokes Node.js modules such as
- fs
- child_process
- process
From here, an attacker can read files, spawn shells, or run system commands.
Impact
CVE-2025-55182 is extremely severe because:
It enables unauthenticated RCE: No login or prior access needed.
It widely affects adopted frameworks: Applications using RSC in Next.js were especially vulnerable.
Exploitation is trivial once the endpoint is exposed: PoCs require only simple multipart requests.
A compromised server may leak:
- environment variables
- database credentials
- source code
- system files
- cloud metadata
Attackers can pivot into the infrastructure: Compromised Node.js processes can be used to establish persistence.
Mitigation / Recommendations
Apply the official patches:-
Upgrade to the latest versions of:
- React
- Next.js
- Any framework using RSC/Flight protocol
Disable or restrict RSC endpoints if unused: Many applications don’t actually rely on RSC features.
Apply WAF/IPS rules:
Block multipart requests containing:
$1:__proto__
$1:constructor
Isolate affected systems: If you detect exploitation attempts, treat the server as compromised.
Quick Heal Protection
All Seqrite customers are protected from this vulnerability by the following signatures:
HTTP/CVE-2025-55182!VS.50159
HTTP/CVE-2025-55182!VS.50160
HTTP/CVE-2025-55182!VS.50161
HTTP/CVE-2025-55182!VS.50162
The post The CVSS 10 React Vulnerability: CVE-2025-55182 appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.

