Security Flaws in eMagicOne Store Manager for WooCommerce in WordPress (CVE-2025-5058 and CVE-2025-4603)
The eMagicOne Store Manager for WooCommerce plugin is in WordPress used to simplify and improve store management by providing functionality not found in the normal WooCommerce admin interface.
Two serious flaws, CVE-2025-5058 and CVE-2025-4603, were found in the eMagicOne Store Manager for WooCommerce WordPress plugin.Possessing a critical CVSS score of more than 9. Only in certain situations, such as default configurations with a 1:1 password or if the attacker manages to gain legitimate credentials then attacker accomplish remote code execution.
Affected Versions:
- eMagicOne Store Manager for WooCommerce * <=2.5
Vulnerability Details:
- CVE-2025-5058:
The plugin’s remote management protocol endpoint (?connector=bridge), which manages file uploads, is vulnerable. The setimage()’s improper file type validation is the source of the vulnerability. The session key system and default credentials (login=1, password=1) are used by the authentication mechanism.
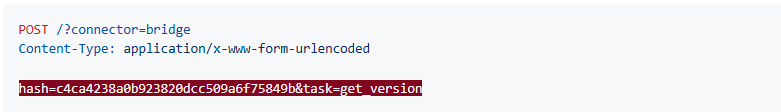
Session Key Acquisition:
Sending a POST request to the bridge endpoint with the hash and a task (such as get_version) yields a session key.
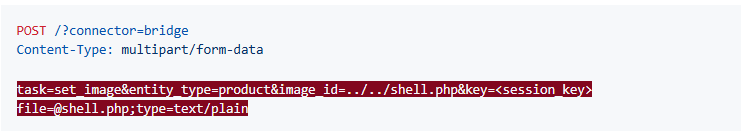
Arbitrary file upload:
An attacker can use the set_image task to upload a file with a valid session key, exploiting the parameters to write whatever file they want.
Real-world Consequences:
This flaw gives attackers the opportunity to upload any file to the server of the compromised site, which could result in remote code execution. When default credentials are left unaltered, unauthenticated attackers can exploit it, which makes the damage very serious. A successful exploitation could lead to a full server compromise, giving attackers access to private data, the ability to run malicious code, or more compromise.
- CVE-2025-4603:
The delete_file() function of the eMagicOne Store Manager for WooCommerce plugin for WordPress lacks sufficient file path validation, making it susceptible to arbitrary file deletion. This enables unauthorized attackers to remove any file from the server, which can easily result in remote code execution if the correct file (like wp-config.php) is removed. Unauthenticated attackers can take advantage of this in default installations.
The remote management protocol endpoint (?connector=bridge) of the plugin, which manages file deletion activities, is the source of the vulnerability. The session key system and default credentials (login=1, password=1) are used by the authentication mechanism. The default authentication hash, md5(‘1’. ‘1’), is computed as follows: c4ca4238a0b923820dcc509a6f75849b. An attacker can use the delete_file task to remove arbitrary files from the WordPress root or any accessible directory after gaining a session key.
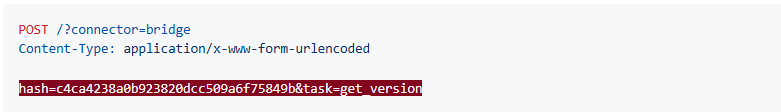
Session Key Acquisition:
Sending a POST request to the bridge endpoint with the hash and a task (such as get_version) yields a session key.
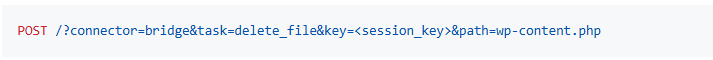
Arbitrary file deletion:
An attacker can use the delete_file task to delete a file if they have a valid session key.
Real-world Consequences:
If this vulnerability is successfully exploited, important server files like wp-config.php may be deleted, potentially disrupting the website and allowing remote code execution. The availability and integrity of the WordPress installation are seriously threatened by the ability to remove arbitrary files.
Countermeasures for both the CVE’s.
- Immediately update their authentication credentials from the default values.
- Update the plugin to the latest version than 1.2.5 is recommended once a patch is available.
- Implement strict file upload validation for CVE-2025-5058.
- Review and restrict server-side file upload permissions for CVE-2025-5058.
Conclusion:
CVE-2025-5058 and CVE-2025-4603 demonstrates how default configurations can become a vector for unintended data exposure. By leveraging improper file handling and lacks of sufficient file path validation an attacker can compromised site which result in remote code execution. Unauthenticated attackers can take advantage of default credentials if they are left unmodified, which can cause significant harm.
The post Security Flaws in eMagicOne Store Manager for WooCommerce in WordPress (CVE-2025-5058 and CVE-2025-4603) appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.

